mirror of
https://github.com/docker/docker-bench-security.git
synced 2025-06-28 07:36:43 +00:00
Compare commits
No commits in common. "master" and "v1.2.0" have entirely different histories.
34 changed files with 1485 additions and 4811 deletions
|
|
@ -1,6 +1 @@
|
|||
*
|
||||
!docker-bench-security.sh
|
||||
!functions/
|
||||
!tests/
|
||||
!log/
|
||||
log/*
|
||||
.git
|
||||
|
|
|
|||
19
.github/workflows/issues.yml
vendored
19
.github/workflows/issues.yml
vendored
|
|
@ -1,19 +0,0 @@
|
|||
name: Issue assignment
|
||||
|
||||
on:
|
||||
issues:
|
||||
types: [opened]
|
||||
|
||||
permissions:
|
||||
contents: read
|
||||
|
||||
jobs:
|
||||
auto-assign:
|
||||
permissions:
|
||||
issues: write
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- name: 'auto-assign issue'
|
||||
uses: pozil/auto-assign-issue@74b9f64cc1a08f99358061073e243a4c3d7dd5c4 # v1.11.0
|
||||
with:
|
||||
assignees: konstruktoid
|
||||
80
.github/workflows/slsa.yml
vendored
80
.github/workflows/slsa.yml
vendored
|
|
@ -1,80 +0,0 @@
|
|||
---
|
||||
name: SLSA
|
||||
on:
|
||||
push:
|
||||
release:
|
||||
permissions:
|
||||
contents: write
|
||||
types: [published, released]
|
||||
|
||||
permissions:
|
||||
contents: read
|
||||
|
||||
jobs:
|
||||
build:
|
||||
outputs:
|
||||
hashes: ${{ steps.hash.outputs.hashes }}
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- name: Harden Runner
|
||||
uses: step-security/harden-runner@63c24ba6bd7ba022e95695ff85de572c04a18142 # v2.7.0
|
||||
with:
|
||||
egress-policy: audit
|
||||
|
||||
- run: echo "REPOSITORY_NAME=$(echo '${{ github.repository }}' | awk -F '/' '{print $2}')" >> $GITHUB_ENV
|
||||
shell: bash
|
||||
|
||||
- name: Checkout repository
|
||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
||||
|
||||
- name: Build artifacts
|
||||
run: |
|
||||
find *.sh functions/* tests/* Dockerfile Vagrantfile -exec sha256sum {} \; > ${{ env.REPOSITORY_NAME }}.sha256
|
||||
|
||||
- name: Generate hashes
|
||||
shell: bash
|
||||
id: hash
|
||||
run: |
|
||||
echo "hashes=$(sha256sum ${{ env.REPOSITORY_NAME }}.sha256 | base64 -w0)" >> "$GITHUB_OUTPUT"
|
||||
|
||||
- name: Upload ${{ env.REPOSITORY_NAME }}.sha256
|
||||
uses: actions/upload-artifact@5d5d22a31266ced268874388b861e4b58bb5c2f3 # v4.3.1
|
||||
with:
|
||||
name: ${{ env.REPOSITORY_NAME }}.sha256
|
||||
path: ${{ env.REPOSITORY_NAME }}.sha256
|
||||
if-no-files-found: error
|
||||
retention-days: 5
|
||||
|
||||
provenance:
|
||||
needs: [build]
|
||||
permissions:
|
||||
actions: read
|
||||
id-token: write
|
||||
contents: write
|
||||
uses: slsa-framework/slsa-github-generator/.github/workflows/generator_generic_slsa3.yml@v1.10.0
|
||||
with:
|
||||
base64-subjects: "${{ needs.build.outputs.hashes }}"
|
||||
upload-assets: ${{ startsWith(github.ref, 'refs/tags/') }}
|
||||
|
||||
release:
|
||||
permissions:
|
||||
actions: read
|
||||
id-token: write
|
||||
contents: write
|
||||
needs: [build, provenance]
|
||||
runs-on: ubuntu-latest
|
||||
if: startsWith(github.ref, 'refs/tags/')
|
||||
steps:
|
||||
- run: echo "REPOSITORY_NAME=$(echo '${{ github.repository }}' | awk -F '/' '{print $2}')" >> $GITHUB_ENV
|
||||
shell: bash
|
||||
|
||||
- name: Download ${{ env.REPOSITORY_NAME }}.sha256
|
||||
uses: actions/download-artifact@c850b930e6ba138125429b7e5c93fc707a7f8427 # v4.1.4
|
||||
with:
|
||||
name: ${{ env.REPOSITORY_NAME }}.sha256
|
||||
|
||||
- name: Upload asset
|
||||
uses: softprops/action-gh-release@9d7c94cfd0a1f3ed45544c887983e9fa900f0564 # v2.0.4
|
||||
with:
|
||||
files: |
|
||||
${{ env.REPOSITORY_NAME }}.sha256
|
||||
4
.gitignore
vendored
4
.gitignore
vendored
|
|
@ -1,3 +1 @@
|
|||
log/*
|
||||
*.swp*
|
||||
.vagrant/
|
||||
*.log
|
||||
|
|
|
|||
|
|
@ -3,56 +3,49 @@
|
|||
Want to hack on Docker Bench? Awesome! Here are instructions to get you
|
||||
started.
|
||||
|
||||
The Docker Bench for Security is a part of the [Docker](https://www.docker.com)
|
||||
project, and follows the same rules and principles. If you're already familiar
|
||||
with the way Docker does things, you'll feel right at home.
|
||||
The Docker Bench for Security is a part of the [Docker](https://www.docker.com) project, and follows
|
||||
the same rules and principles. If you're already familiar with the way
|
||||
Docker does things, you'll feel right at home.
|
||||
|
||||
Otherwise, go read
|
||||
[Contribute to the Moby Project](https://github.com/moby/moby/blob/master/CONTRIBUTING.md).
|
||||
[Docker's contributions guidelines](https://github.com/docker/docker/blob/master/CONTRIBUTING.md).
|
||||
|
||||
## Development Environment Setup
|
||||
### Development Environment Setup
|
||||
|
||||
### Start hacking
|
||||
The only thing you need to hack on Docker Bench for Security is a POSIX 2004 compliant shell. We try to keep the project compliant for maximum portability
|
||||
|
||||
#### Start hacking
|
||||
|
||||
You can build the container that wraps the docker-bench for security:
|
||||
|
||||
```sh
|
||||
git clone git@github.com:docker/docker-bench-security.git
|
||||
cd docker-bench-security
|
||||
docker build -t docker-bench-security .
|
||||
✗ git clone git@github.com:docker/docker-bench-security.git
|
||||
✗ cd docker-bench-security
|
||||
✗ docker build -t docker-bench-security .
|
||||
```
|
||||
|
||||
Or you can simply run the shell script locally:
|
||||
|
||||
```sh
|
||||
git clone git@github.com:docker/docker-bench-security.git
|
||||
cd docker-bench-security
|
||||
sudo sh docker-bench-security.sh
|
||||
✗ git clone git@github.com:docker/docker-bench-security.git
|
||||
✗ cd docker-bench-security
|
||||
✗ sh docker-bench-security.sh
|
||||
```
|
||||
|
||||
The Docker Bench has the main script called `docker-bench-security.sh`.
|
||||
This is the main script that checks for all the dependencies, deals with
|
||||
command line arguments and loads all the tests.
|
||||
The Docker Bench has the main script called `docker-bench-security.sh`. This is the main script that checks for all the dependencies, deals with command line arguments and loads all the tests.
|
||||
|
||||
The tests are split into the following files:
|
||||
The tests are split in 6 different files:
|
||||
|
||||
```sh
|
||||
✗ tree tests/
|
||||
tests/
|
||||
├── 1_host_configuration.sh
|
||||
├── 2_docker_daemon_configuration.sh
|
||||
├── 3_docker_daemon_configuration_files.sh
|
||||
├── 4_container_images.sh
|
||||
├── 5_container_runtime.sh
|
||||
├── 6_docker_security_operations.sh
|
||||
├── 7_docker_swarm_configuration.sh
|
||||
├── 8_docker_enterprise_configuration.sh
|
||||
└── 99_community_checks.sh
|
||||
└── 6_docker_security_operations.sh
|
||||
```
|
||||
|
||||
To modify the Docker Bench for Security you should first clone the repository,
|
||||
make your changes, check your code with `shellcheck`, or similar tools, and
|
||||
then sign off on your commits. After that feel free to send us a pull request
|
||||
with the changes.
|
||||
To modify the Docker Bench for Security you should first clone the repository, make your changes, check your code with `shellcheck`, `checkbashisms` or similar tools, and then sign off on your commits. After that feel free to send us a pull-request with the changes.
|
||||
|
||||
While this tool was inspired by the [CIS Docker 1.11.0 benchmark](https://www.cisecurity.org/benchmark/docker/)
|
||||
and its successors, feel free to add new tests.
|
||||
While this tool is inspired by the [CIS Docker 1.11.0 benchmark](https://benchmarks.cisecurity.org/downloads/show-single/index.cfm?file=docker16.110), feel free to add new tests. We will try to turn dockerbench.com into a list of good community benchmarks for both security and performance, and we would love community contributions.
|
||||
|
|
|
|||
|
|
@ -1,58 +0,0 @@
|
|||
The following people, listed in alphabetical order, have contributed to docker-bench-security:
|
||||
|
||||
* alberto <alberto@tutum.co>
|
||||
* Andreas Stieger <astieger@suse.com>
|
||||
* Anthony Roger <aroger@softwaymedical.fr>
|
||||
* Aurélien Gasser <aurelien.gasser@gmail.com>
|
||||
* binary <binary@webdev.fritz.box>
|
||||
* Boris Gorbylev <ekho@ekho.name>
|
||||
* Cheng-Li Jerry Ma <chengli.ma@gmail.com>
|
||||
* Csaba Palfi <csaba@palfi.me>
|
||||
* Daniele Marcocci <daniele.marcocci@par-tec.it>
|
||||
* Dhawal Patel <dhawal.patel@nordstrom.com>
|
||||
* Diogo Monica <diogo@docker.com>
|
||||
* Diogo Mónica <diogo.monica@gmail.com>
|
||||
* Ernst de Haan <ernst@ernstdehaan.com>
|
||||
* HuKeping <hukeping@huawei.com>
|
||||
* Ivan Angelov <iangelov@users.noreply.github.com>
|
||||
* J0WI <J0WI@users.noreply.github.com>
|
||||
* jammasterj89 <jammasterj89@gmail.com>
|
||||
* Jessica Frazelle <princess@docker.com>
|
||||
* Joachim Lusiardi <jlusiardi@users.noreply.github.com>
|
||||
* Joachim Lusiardi <joachim@lusiardi.de>
|
||||
* Joachim Lusiardi <shing19m@dev1.lusiardi.de>
|
||||
* Joe Williams <joe.williams@github.com>
|
||||
* Julien Garcia Gonzalez <julien@giantswarm.io>
|
||||
* Jürgen Hermann <jh@web.de>
|
||||
* kakakakakku <y.yoshida22@gmail.com>
|
||||
* Karol Babioch <kbabioch@suse.de>
|
||||
* Kevin Lim <kevin.lim@sap.com>
|
||||
* kevinll <imhael@gmail.com>
|
||||
* Liron Levin <liron@twistlock.com>
|
||||
* liron-l <levinlir@gmail.com>
|
||||
* LorensK <LorensK@users.noreply.github.com>
|
||||
* lusitania <lusitania@users.noreply.github.com>
|
||||
* Maik Ellerbrock <opensource@frapsoft.com>
|
||||
* Mark Stemm <mark.stemm@gmail.com>
|
||||
* Matt Fellows <matt.fellows@onegeek.com.au>
|
||||
* Michael Crosby <crosbymichael@gmail.com>
|
||||
* Michael Stahn <michael.stahn.42@gmail.com>
|
||||
* Mike Ritter <mike.ritter@target.com>
|
||||
* Mr. Secure <ben.github@mrsecure.org>
|
||||
* MrSecure <MrSecure@users.noreply.github.com>
|
||||
* Nigel Brown <nigel@windsock.io>
|
||||
* Paul Czarkowski <username.taken@gmail.com>
|
||||
* Paul Morgan <jumanjiman@gmail.com>
|
||||
* Pete Sellars <psellars@gmail.com>
|
||||
* Peter <lusitania@users.noreply.github.com>
|
||||
* Ravi Kumar Vadapalli <vadapalli.ravikumar@gmail.com>
|
||||
* Scott McCarty <scott.mccarty@gmail.com>
|
||||
* Sebastiaan van Stijn <github@gone.nl>
|
||||
* telepresencebot2 <telepresencebot2@users.noreply.github.com>
|
||||
* Thomas Sjögren <konstruktoid@users.noreply.github.com>
|
||||
* Tom Partington <tom.partington@cevo.com.au>
|
||||
* Werner Buck <wernerbuck@gmail.com>
|
||||
* will Farrell <willfarrell@users.noreply.github.com>
|
||||
* Zvi "Viz" Effron <zeffron@riotgames.com>
|
||||
|
||||
This list was generated Tue Nov 5 09:45:35 UTC 2019.
|
||||
40
Dockerfile
40
Dockerfile
|
|
@ -1,20 +1,32 @@
|
|||
FROM alpine:3.18@sha256:eece025e432126ce23f223450a0326fbebde39cdf496a85d8c016293fc851978
|
||||
FROM alpine:3.5
|
||||
|
||||
LABEL \
|
||||
org.label-schema.name="docker-bench-security" \
|
||||
org.label-schema.url="https://dockerbench.com" \
|
||||
org.label-schema.vcs-url="https://github.com/docker/docker-bench-security.git"
|
||||
LABEL org.label-schema.name="docker-bench-security" \
|
||||
org.label-schema.url="https://dockerbench.com" \
|
||||
org.label-schema.vcs-url="https://github.com/docker/docker-bench-security.git"
|
||||
|
||||
RUN apk add --no-cache iproute2 \
|
||||
docker-cli \
|
||||
dumb-init \
|
||||
jq
|
||||
ENV VERSION 1.12.6
|
||||
ENV SHA256 cadc6025c841e034506703a06cf54204e51d0cadfae4bae62628ac648d82efdd
|
||||
|
||||
COPY . /usr/local/bin/
|
||||
WORKDIR /usr/bin
|
||||
|
||||
HEALTHCHECK CMD exit 0
|
||||
RUN apk update && \
|
||||
apk upgrade && \
|
||||
apk --update add coreutils wget ca-certificates && \
|
||||
wget https://get.docker.com/builds/Linux/x86_64/docker-$VERSION.tgz && \
|
||||
wget https://get.docker.com/builds/Linux/x86_64/docker-$VERSION.tgz.sha256 && \
|
||||
sha256sum -c docker-$VERSION.tgz.sha256 && \
|
||||
echo "$SHA256 docker-$VERSION.tgz" | sha256sum -c - && \
|
||||
tar -xzvf docker-$VERSION.tgz -C /tmp && \
|
||||
mv /tmp/docker/docker . && \
|
||||
chmod u+x docker* && \
|
||||
rm -rf /tmp/docker* && \
|
||||
apk del wget ca-certificates && \
|
||||
rm -rf /var/cache/apk/* docker-$VERSION.tgz docker-$VERSION.tgz.sha256
|
||||
|
||||
WORKDIR /usr/local/bin
|
||||
RUN mkdir /docker-bench-security
|
||||
|
||||
ENTRYPOINT [ "/usr/bin/dumb-init", "/bin/sh", "docker-bench-security.sh" ]
|
||||
CMD [""]
|
||||
COPY . /docker-bench-security
|
||||
|
||||
WORKDIR /docker-bench-security
|
||||
|
||||
ENTRYPOINT ["/bin/sh", "docker-bench-security.sh"]
|
||||
|
|
|
|||
|
|
@ -30,5 +30,5 @@
|
|||
|
||||
[people.konstruktoid]
|
||||
Name = "Thomas Sjögren"
|
||||
Email = "thomas.sjogren@protonmail.com"
|
||||
Email = "thomas.sjogren@outlook.com"
|
||||
GitHub = "konstruktoid"
|
||||
|
|
|
|||
184
README.md
184
README.md
|
|
@ -1,51 +1,68 @@
|
|||
# Docker Bench for Security
|
||||
|
||||

|
||||

|
||||
|
||||
The Docker Bench for Security is a script that checks for dozens of common best-practices around deploying Docker containers in production. The tests are all automated, and are based on the [CIS Docker Benchmark v1.6.0](https://www.cisecurity.org/benchmark/docker/).
|
||||
The Docker Bench for Security is a script that checks for dozens of common
|
||||
best-practices around deploying Docker containers in production. The tests are
|
||||
all automated, and are inspired by the [CIS Docker 1.12 Benchmark](https://benchmarks.cisecurity.org/tools2/docker/CIS_Docker_1.12.0_Benchmark_v1.0.0.pdf).
|
||||
We are releasing this as a follow-up to our [Understanding Docker Security and Best Practices](https://blog.docker.com/2015/05/understanding-docker-security-and-best-practices/)
|
||||
blog post.
|
||||
|
||||
We are making this available as an open-source utility so the Docker community can have an easy way to self-assess their hosts and Docker containers against this benchmark.
|
||||
|
||||
Release | CIS |
|
||||
:---:|:---:|
|
||||
1.6.0|1.6.0|
|
||||
1.5.0|1.5.0|
|
||||
1.3.6|1.4.0|
|
||||
1.3.5|1.2.0|
|
||||
1.3.3|1.1.0|
|
||||
1.3.0|1.13.0|
|
||||
We are making this available as an open-source utility so the Docker community
|
||||
can have an easy way to self-assess their hosts and docker containers against
|
||||
this benchmark.
|
||||
|
||||
## Running Docker Bench for Security
|
||||
|
||||
### Run from your base host
|
||||
We packaged docker bench as a small container for your convenience. Note that
|
||||
this container is being run with a *lot* of privilege -- sharing the host's
|
||||
filesystem, pid and network namespaces, due to portions of the benchmark
|
||||
applying to the running host. Don't forget to adjust the shared volumes
|
||||
according to your operating system, it may not for example use systemd.
|
||||
|
||||
You can simply run this script from your base host by running:
|
||||
The easiest way to run your hosts against the Docker Bench for Security is by
|
||||
running our pre-built container:
|
||||
|
||||
```sh
|
||||
docker run -it --net host --pid host --cap-add audit_control \
|
||||
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
|
||||
-v /var/lib:/var/lib \
|
||||
-v /var/run/docker.sock:/var/run/docker.sock \
|
||||
-v /usr/lib/systemd:/usr/lib/systemd \
|
||||
-v /etc:/etc --label docker_bench_security \
|
||||
docker/docker-bench-security
|
||||
```
|
||||
|
||||
Docker bench requires Docker 1.10.0 or later in order to run.
|
||||
|
||||
Also note that the default image and `Dockerfile` uses `FROM: alpine` which
|
||||
doesn't contain `auditctl`, this will generate errors in section 1.8 to 1.15.
|
||||
Distribution specific Dockerfiles that fixes this issue are available in the
|
||||
[distros directory](https://github.com/docker/docker-bench-security/tree/master/distros).
|
||||
|
||||
The [distribution specific Dockerfiles](https://github.com/docker/docker-bench-security/tree/master/distros)
|
||||
may also help if the distribution you're using haven't yet shipped Docker
|
||||
version 1.10.0 or later.
|
||||
|
||||
## Building Docker Bench for Security
|
||||
|
||||
If you wish to build and run this container yourself, you can follow the
|
||||
following steps:
|
||||
|
||||
```sh
|
||||
git clone https://github.com/docker/docker-bench-security.git
|
||||
cd docker-bench-security
|
||||
sudo sh docker-bench-security.sh
|
||||
docker build -t docker-bench-security .
|
||||
docker run -it --net host --pid host --cap-add audit_control \
|
||||
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
|
||||
-v /var/lib:/var/lib \
|
||||
-v /var/run/docker.sock:/var/run/docker.sock \
|
||||
-v /usr/lib/systemd:/usr/lib/systemd \
|
||||
-v /etc:/etc --label docker_bench_security \
|
||||
docker-bench-security
|
||||
```
|
||||
|
||||
> Note: [`jq`](https://jqlang.github.io/jq/) is an optional but recommended dependency.
|
||||
|
||||
### Run with Docker
|
||||
|
||||
#### Building Docker image
|
||||
|
||||
You have two options if you wish to build and run this container yourself:
|
||||
|
||||
1. Use Docker Build:
|
||||
|
||||
```sh
|
||||
git clone https://github.com/docker/docker-bench-security.git
|
||||
cd docker-bench-security
|
||||
docker build --no-cache -t docker-bench-security .
|
||||
```
|
||||
|
||||
Followed by an appropriate `docker run` command as stated below.
|
||||
|
||||
2. Use Docker Compose:
|
||||
or use [Docker Compose](https://docs.docker.com/compose/):
|
||||
|
||||
```sh
|
||||
git clone https://github.com/docker/docker-bench-security.git
|
||||
|
|
@ -53,100 +70,13 @@ cd docker-bench-security
|
|||
docker-compose run --rm docker-bench-security
|
||||
```
|
||||
|
||||
_Please note that the `docker/docker-bench-security` image is out-of-date and and a manual build is required. See [#405](https://github.com/docker/docker-bench-security/issues/405) for more information._
|
||||
|
||||
Note that this container is being run with a *lot* of privilege -- sharing the host's filesystem, pid and network namespaces, due to portions of the benchmark applying to the running host.
|
||||
|
||||
### Using the container
|
||||
Also, this script can also be simply run from your base host by running:
|
||||
|
||||
```sh
|
||||
docker run --rm --net host --pid host --userns host --cap-add audit_control \
|
||||
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
|
||||
-v /etc:/etc:ro \
|
||||
-v /usr/bin/containerd:/usr/bin/containerd:ro \
|
||||
-v /usr/bin/runc:/usr/bin/runc:ro \
|
||||
-v /usr/lib/systemd:/usr/lib/systemd:ro \
|
||||
-v /var/lib:/var/lib:ro \
|
||||
-v /var/run/docker.sock:/var/run/docker.sock:ro \
|
||||
--label docker_bench_security \
|
||||
docker-bench-security
|
||||
git clone https://github.com/docker/docker-bench-security.git
|
||||
cd docker-bench-security
|
||||
sh docker-bench-security.sh
|
||||
```
|
||||
|
||||
Don't forget to adjust the shared volumes according to your operating system.
|
||||
Some examples are:
|
||||
|
||||
1. On Ubuntu the `docker.service` and `docker.secret` files are located in
|
||||
`/lib/systemd/system` folder by default.
|
||||
|
||||
```sh
|
||||
docker run --rm --net host --pid host --userns host --cap-add audit_control \
|
||||
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
|
||||
-v /etc:/etc:ro \
|
||||
-v /lib/systemd/system:/lib/systemd/system:ro \
|
||||
-v /usr/bin/containerd:/usr/bin/containerd:ro \
|
||||
-v /usr/bin/runc:/usr/bin/runc:ro \
|
||||
-v /usr/lib/systemd:/usr/lib/systemd:ro \
|
||||
-v /var/lib:/var/lib:ro \
|
||||
-v /var/run/docker.sock:/var/run/docker.sock:ro \
|
||||
--label docker_bench_security \
|
||||
docker-bench-security
|
||||
```
|
||||
|
||||
2. The /etc/hostname file is missing on macOS, so it will need to be created first. Also, `Docker Desktop` on macOS doesn't have `/usr/lib/systemd` or the above Docker
|
||||
binaries.
|
||||
|
||||
```sh
|
||||
sudo touch /etc/hostname
|
||||
|
||||
docker run --rm --net host --pid host --userns host --cap-add audit_control \
|
||||
-e DOCKER_CONTENT_TRUST=$DOCKER_CONTENT_TRUST \
|
||||
-v /etc:/etc \
|
||||
-v /var/lib:/var/lib:ro \
|
||||
-v /var/run/docker.sock:/var/run/docker.sock:ro \
|
||||
--label docker_bench_security \
|
||||
docker-bench-security
|
||||
```
|
||||
|
||||
### Note
|
||||
|
||||
Docker bench requires Docker 1.13.0 or later in order to run.
|
||||
|
||||
Note that when distributions don't contain `auditctl`, the audit tests will check `/etc/audit/audit.rules` to see if a rule is present instead.
|
||||
|
||||
### Docker Bench for Security options
|
||||
|
||||
```sh
|
||||
-b optional Do not print colors
|
||||
-h optional Print this help message
|
||||
-l FILE optional Log output in FILE, inside container if run using docker
|
||||
-u USERS optional Comma delimited list of trusted docker user(s)
|
||||
-c CHECK optional Comma delimited list of specific check(s) id
|
||||
-e CHECK optional Comma delimited list of specific check(s) id to exclude
|
||||
-i INCLUDE optional Comma delimited list of patterns within a container or image name to check
|
||||
-x EXCLUDE optional Comma delimited list of patterns within a container or image name to exclude from check
|
||||
-t LABEL optional Comma delimited list of labels within a container or image to check
|
||||
-n LIMIT optional In JSON output, when reporting lists of items (containers, images, etc.), limit the number of reported items to LIMIT. Default 0 (no limit).
|
||||
-p PRINT optional Disable the printing of remediation measures. Default: print remediation measures.
|
||||
```
|
||||
|
||||
By default the Docker Bench for Security script will run all available CIS tests and produce
|
||||
logs in the log folder from current directory, named `docker-bench-security.log.json` and
|
||||
`docker-bench-security.log`.
|
||||
|
||||
If the docker container is used then the log files will be created inside the container in location `/usr/local/bin/log/`. If you wish to access them from the host after the container has been run you will need to mount a volume for storing them in.
|
||||
|
||||
The CIS based checks are named `check_<section>_<number>`, e.g. `check_2_6` and community contributed checks are named `check_c_<number>`.
|
||||
|
||||
`sh docker-bench-security.sh -c check_2_2` will only run check `2.2 Ensure the logging level is set to 'info'`.
|
||||
|
||||
`sh docker-bench-security.sh -e check_2_2` will run all available checks except `2.2 Ensure the logging level is set to 'info'`.
|
||||
|
||||
`sh docker-bench-security.sh -e docker_enterprise_configuration` will run all available checks except the docker_enterprise_configuration group
|
||||
|
||||
`sh docker-bench-security.sh -e docker_enterprise_configuration,check_2_2` will run all available checks except the docker_enterprise_configuration group and `2.2 Ensure the logging level is set to 'info'`
|
||||
|
||||
`sh docker-bench-security.sh -c container_images,container_runtime` will run just the container_images and container_runtime checks
|
||||
|
||||
`sh docker-bench-security.sh -c container_images -e check_4_5` will run just the container_images checks except `4.5 Ensure Content trust for Docker is Enabled`
|
||||
|
||||
Note that when submitting checks, provide information why it is a reasonable test to add and please include some kind of official documentation verifying that information.
|
||||
This script was build to be POSIX 2004 compliant, so it should be portable
|
||||
across any Unix platform.
|
||||
|
|
|
|||
19
Vagrantfile
vendored
19
Vagrantfile
vendored
|
|
@ -1,19 +0,0 @@
|
|||
Vagrant.configure("2") do |config|
|
||||
config.vbguest.installer_options = { allow_kernel_upgrade: true }
|
||||
config.vm.provider "virtualbox" do |v|
|
||||
v.memory = 2048
|
||||
v.cpus = 2
|
||||
v.customize ["modifyvm", :id, "--uart1", "0x3F8", "4"]
|
||||
v.customize ["modifyvm", :id, "--uartmode1", "file", File::NULL]
|
||||
end
|
||||
|
||||
config.vm.define "jammy" do |jammy|
|
||||
jammy.ssh.extra_args = ["-o","ConnectTimeout=600"]
|
||||
jammy.ssh.insert_key = true
|
||||
jammy.vm.boot_timeout = 600
|
||||
jammy.vm.box = "ubuntu/jammy64"
|
||||
jammy.vm.hostname = "jammy"
|
||||
jammy.vm.provision "shell",
|
||||
inline: "apt-get update && curl -sSL get.docker.com | sh && addgroup vagrant docker"
|
||||
end
|
||||
end
|
||||
BIN
benchmark_log.png
Normal file
BIN
benchmark_log.png
Normal file
Binary file not shown.
|
After 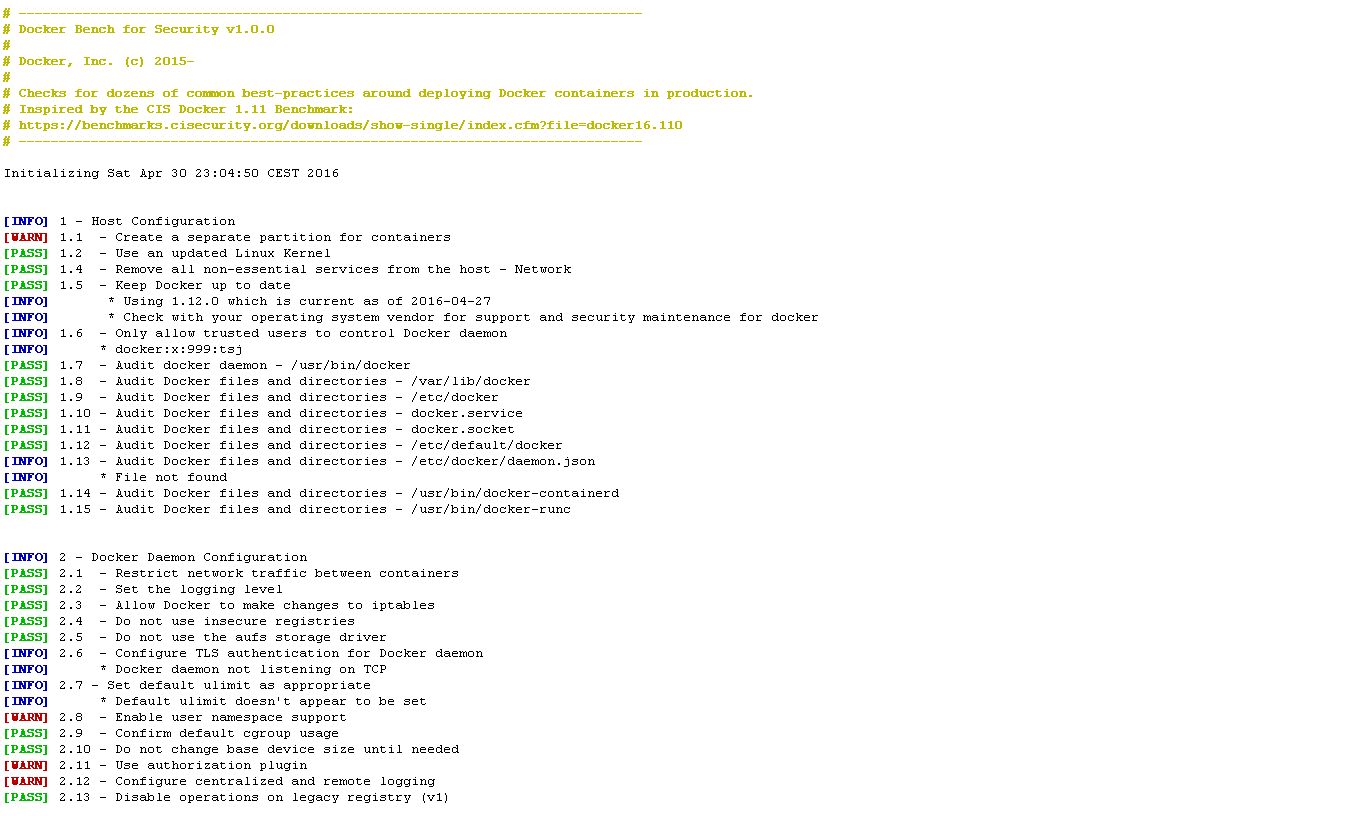
(image error) Size: 66 KiB |
32
distros/Dockerfile.alpine
Normal file
32
distros/Dockerfile.alpine
Normal file
|
|
@ -0,0 +1,32 @@
|
|||
FROM alpine:3.5
|
||||
|
||||
LABEL org.label-schema.name="docker-bench-security" \
|
||||
org.label-schema.url="https://dockerbench.com" \
|
||||
org.label-schema.vcs-url="https://github.com/docker/docker-bench-security.git"
|
||||
|
||||
ENV VERSION 1.12.6
|
||||
ENV SHA256 cadc6025c841e034506703a06cf54204e51d0cadfae4bae62628ac648d82efdd
|
||||
|
||||
WORKDIR /usr/bin
|
||||
|
||||
RUN apk update && \
|
||||
apk upgrade && \
|
||||
apk --update add coreutils wget ca-certificates && \
|
||||
wget https://get.docker.com/builds/Linux/x86_64/docker-$VERSION.tgz && \
|
||||
wget https://get.docker.com/builds/Linux/x86_64/docker-$VERSION.tgz.sha256 && \
|
||||
sha256sum -c docker-$VERSION.tgz.sha256 && \
|
||||
echo "$SHA256 docker-$VERSION.tgz" | sha256sum -c - && \
|
||||
tar -xzvf docker-$VERSION.tgz -C /tmp && \
|
||||
mv /tmp/docker/docker . && \
|
||||
chmod u+x docker* && \
|
||||
rm -rf /tmp/docker* && \
|
||||
apk del wget ca-certificates && \
|
||||
rm -rf /var/cache/apk/* docker-$VERSION.tgz docker-$VERSION.tgz.sha256
|
||||
|
||||
RUN mkdir /docker-bench-security
|
||||
|
||||
COPY . /docker-bench-security
|
||||
|
||||
WORKDIR /docker-bench-security
|
||||
|
||||
ENTRYPOINT ["/bin/sh", "docker-bench-security.sh"]
|
||||
15
distros/Dockerfile.centos
Normal file
15
distros/Dockerfile.centos
Normal file
|
|
@ -0,0 +1,15 @@
|
|||
# REPOSITORY https://github.com/fatherlinux/docker-bench-security
|
||||
|
||||
FROM centos
|
||||
|
||||
MAINTAINER smccarty@redhat.com
|
||||
|
||||
RUN yum install -y docker net-tools audit procps-ng; yum clean all
|
||||
|
||||
RUN mkdir /docker-bench-security
|
||||
|
||||
COPY . /docker-bench-security
|
||||
|
||||
WORKDIR /docker-bench-security
|
||||
|
||||
ENTRYPOINT ["/bin/sh", "docker-bench-security.sh"]
|
||||
24
distros/Dockerfile.debian
Normal file
24
distros/Dockerfile.debian
Normal file
|
|
@ -0,0 +1,24 @@
|
|||
FROM debian:sid
|
||||
|
||||
LABEL org.label-schema.name="docker-bench-security" \
|
||||
org.label-schema.url="https://github.com/konstruktoid/docker-bench-security" \
|
||||
org.label-schema.vcs-url="https://github.com/konstruktoid/docker-bench-security.git"
|
||||
|
||||
RUN \
|
||||
apt-get update && \
|
||||
apt-get -y upgrade && \
|
||||
apt-get -y install auditd ca-certificates docker.io \
|
||||
gawk net-tools procps --no-install-recommends && \
|
||||
apt-get -y clean && \
|
||||
apt-get -y autoremove && \
|
||||
rm -rf /var/lib/apt/lists/* \
|
||||
/usr/share/doc /usr/share/doc-base \
|
||||
/usr/share/man /usr/share/locale /usr/share/zoneinfo
|
||||
|
||||
RUN mkdir /docker-bench-security
|
||||
|
||||
COPY . /docker-bench-security
|
||||
|
||||
WORKDIR /docker-bench-security
|
||||
|
||||
ENTRYPOINT ["/bin/sh", "docker-bench-security.sh"]
|
||||
15
distros/Dockerfile.openSUSE
Normal file
15
distros/Dockerfile.openSUSE
Normal file
|
|
@ -0,0 +1,15 @@
|
|||
# REPOSITORY https://github.com/docker/docker-bench-security
|
||||
|
||||
FROM opensuse
|
||||
|
||||
MAINTAINER security@suse.com
|
||||
|
||||
RUN zypper -n in docker net-tools audit
|
||||
|
||||
RUN mkdir /docker-bench-security
|
||||
|
||||
COPY . /docker-bench-security
|
||||
|
||||
WORKDIR /docker-bench-security
|
||||
|
||||
ENTRYPOINT ["/bin/sh", "docker-bench-security.sh"]
|
||||
18
distros/Dockerfile.rhel
Normal file
18
distros/Dockerfile.rhel
Normal file
|
|
@ -0,0 +1,18 @@
|
|||
# REPOSITORY https://github.com/fatherlinux/docker-bench-security
|
||||
|
||||
FROM rhel7
|
||||
|
||||
MAINTAINER smccarty@redhat.com
|
||||
|
||||
RUN yum install -y yum-utils; yum clean all
|
||||
RUN yum-config-manager --disable "*" &>/dev/null
|
||||
RUN yum-config-manager --enable rhel-7-server-rpms --enable rhel-7-server-extras-rpms
|
||||
RUN yum install -y docker net-tools audit procps-ng; yum clean all
|
||||
|
||||
RUN mkdir /docker-bench-security
|
||||
|
||||
COPY . /docker-bench-security
|
||||
|
||||
WORKDIR /docker-bench-security
|
||||
|
||||
ENTRYPOINT ["/bin/sh", "docker-bench-security.sh"]
|
||||
18
distros/README.md
Normal file
18
distros/README.md
Normal file
|
|
@ -0,0 +1,18 @@
|
|||
# Distribution specific Dockerfiles
|
||||
|
||||
## Requirements
|
||||
|
||||
### Dockerfile name
|
||||
The format should be `Dockerfile.{distribution name}`.
|
||||
|
||||
### Keep your images up-to-date
|
||||
Use the distribution package manager to keep your image up-to-date.
|
||||
|
||||
### REPOSITORY
|
||||
Add a `REPOSITORY` comment with the URL to your GitHub repository where the Dockerfile is present.
|
||||
`# REPOSITORY <GitHub repository>`
|
||||
|
||||
### MAINTAINER
|
||||
Add the `MAINTAINER` instruction and your contact details, GitHub aliases are acceptable.
|
||||
|
||||
For an example Dockerfile, please refer to `Dockerfile.alpine`.
|
||||
|
|
@ -1,222 +1,96 @@
|
|||
#!/bin/bash
|
||||
# --------------------------------------------------------------------------------------------
|
||||
# Docker Bench for Security
|
||||
#!/bin/sh
|
||||
# ------------------------------------------------------------------------------
|
||||
# Docker Bench for Security v1.2.0
|
||||
#
|
||||
# Docker, Inc. (c) 2015-2022
|
||||
# Docker, Inc. (c) 2015-
|
||||
#
|
||||
# Checks for dozens of common best-practices around deploying Docker containers in production.
|
||||
# --------------------------------------------------------------------------------------------
|
||||
|
||||
version='1.6.0'
|
||||
|
||||
LIBEXEC="." # Distributions can change this to /usr/libexec or similar.
|
||||
# Inspired by the CIS Docker 1.12 Benchmark.
|
||||
# ------------------------------------------------------------------------------
|
||||
|
||||
# Load dependencies
|
||||
. $LIBEXEC/functions/functions_lib.sh
|
||||
. $LIBEXEC/functions/helper_lib.sh
|
||||
. ./output_lib.sh
|
||||
. ./helper_lib.sh
|
||||
|
||||
# Setup the paths
|
||||
this_path=$(abspath "$0") ## Path of this file including filename
|
||||
myname=$(basename "${this_path%.*}") ## file name of this script.
|
||||
this_path=$(abspath "$0") ## Path of this file including filenamel
|
||||
myname=$(basename "${this_path}") ## file name of this script.
|
||||
|
||||
readonly version
|
||||
readonly this_path
|
||||
readonly myname
|
||||
|
||||
export PATH="$PATH:/bin:/sbin:/usr/bin:/usr/local/bin:/usr/sbin/"
|
||||
export PATH=/bin:/sbin:/usr/bin:/usr/local/bin:/usr/sbin/
|
||||
|
||||
# Check for required program(s)
|
||||
req_programs 'awk docker grep sed stat tail tee tr wc xargs'
|
||||
req_progs='awk docker grep netstat stat'
|
||||
for p in $req_progs; do
|
||||
command -v "$p" >/dev/null 2>&1 || { printf "%s command not found.\n" "$p"; exit 1; }
|
||||
done
|
||||
|
||||
# Ensure we can connect to docker daemon
|
||||
if ! docker ps -q >/dev/null 2>&1; then
|
||||
docker ps -q >/dev/null 2>&1
|
||||
if [ $? -ne 0 ]; then
|
||||
printf "Error connecting to docker daemon (does docker ps work?)\n"
|
||||
exit 1
|
||||
fi
|
||||
|
||||
usage () {
|
||||
cat <<EOF
|
||||
Docker Bench for Security - Docker, Inc. (c) 2015-$(date +"%Y")
|
||||
Checks for dozens of common best-practices around deploying Docker containers in production.
|
||||
Based on the CIS Docker Benchmark 1.6.0.
|
||||
usage: ${myname} [options]
|
||||
|
||||
Usage: ${myname}.sh [OPTIONS]
|
||||
|
||||
Example:
|
||||
- Only run check "2.2 - Ensure the logging level is set to 'info'":
|
||||
sh docker-bench-security.sh -c check_2_2
|
||||
- Run all available checks except the host_configuration group and "2.8 - Enable user namespace support":
|
||||
sh docker-bench-security.sh -e host_configuration,check_2_8
|
||||
- Run just the container_images checks except "4.5 - Ensure Content trust for Docker is Enabled":
|
||||
sh docker-bench-security.sh -c container_images -e check_4_5
|
||||
|
||||
Options:
|
||||
-b optional Do not print colors
|
||||
-h optional Print this help message
|
||||
-l FILE optional Log output in FILE, inside container if run using docker
|
||||
-u USERS optional Comma delimited list of trusted docker user(s)
|
||||
-c CHECK optional Comma delimited list of specific check(s) id
|
||||
-e CHECK optional Comma delimited list of specific check(s) id to exclude
|
||||
-i INCLUDE optional Comma delimited list of patterns within a container or image name to check
|
||||
-x EXCLUDE optional Comma delimited list of patterns within a container or image name to exclude from check
|
||||
-t LABEL optional Comma delimited list of labels within a container or image to check
|
||||
-n LIMIT optional In JSON output, when reporting lists of items (containers, images, etc.), limit the number of reported items to LIMIT. Default 0 (no limit).
|
||||
-p PRINT optional Print remediation measures. Default: Don't print remediation measures.
|
||||
|
||||
Complete list of checks: <https://github.com/docker/docker-bench-security/blob/master/tests/>
|
||||
Full documentation: <https://github.com/docker/docker-bench-security>
|
||||
Released under the Apache-2.0 License.
|
||||
-l PATH optional Log output in PATH
|
||||
EOF
|
||||
}
|
||||
|
||||
# Default values
|
||||
if [ ! -d log ]; then
|
||||
mkdir log
|
||||
fi
|
||||
|
||||
logger="log/${myname}.log"
|
||||
limit=0
|
||||
printremediation="0"
|
||||
globalRemediation=""
|
||||
|
||||
# Get the flags
|
||||
# If you add an option here, please
|
||||
# remember to update usage() above.
|
||||
while getopts bhl:u:c:e:i:x:t:n:p args
|
||||
while getopts hl: args
|
||||
do
|
||||
case $args in
|
||||
b) nocolor="nocolor";;
|
||||
h) usage; exit 0 ;;
|
||||
l) logger="$OPTARG" ;;
|
||||
u) dockertrustusers="$OPTARG" ;;
|
||||
c) check="$OPTARG" ;;
|
||||
e) checkexclude="$OPTARG" ;;
|
||||
i) include="$OPTARG" ;;
|
||||
x) exclude="$OPTARG" ;;
|
||||
t) labels="$OPTARG" ;;
|
||||
n) limit="$OPTARG" ;;
|
||||
p) printremediation="1" ;;
|
||||
*) usage; exit 1 ;;
|
||||
esac
|
||||
done
|
||||
|
||||
# Load output formating
|
||||
. $LIBEXEC/functions/output_lib.sh
|
||||
|
||||
yell_info
|
||||
|
||||
# Warn if not root
|
||||
if [ "$(id -u)" != "0" ]; then
|
||||
warn "$(yell 'Some tests might require root to run')\n"
|
||||
sleep 3
|
||||
if [ -z "$logger" ]; then
|
||||
logger="${myname}.log"
|
||||
fi
|
||||
|
||||
# Total Score
|
||||
# Warn Scored -1, Pass Scored +1, Not Score -0
|
||||
yell "# ------------------------------------------------------------------------------
|
||||
# Docker Bench for Security v1.2.0
|
||||
#
|
||||
# Docker, Inc. (c) 2015-
|
||||
#
|
||||
# Checks for dozens of common best-practices around deploying Docker containers in production.
|
||||
# Inspired by the CIS Docker 1.12 Benchmark.
|
||||
# ------------------------------------------------------------------------------"
|
||||
|
||||
totalChecks=0
|
||||
currentScore=0
|
||||
# Warn if not root
|
||||
ID=$(id -u)
|
||||
if [ "x$ID" != "x0" ]; then
|
||||
warn "Some tests might require root to run"
|
||||
sleep 3
|
||||
fi
|
||||
|
||||
logit "Initializing $(date +%Y-%m-%dT%H:%M:%S%:z)\n"
|
||||
beginjson "$version" "$(date +%s)"
|
||||
logit "Initializing $(date)\n"
|
||||
|
||||
# Load all the tests from tests/ and run them
|
||||
main () {
|
||||
logit "\n${bldylw}Section A - Check results${txtrst}"
|
||||
|
||||
# Get configuration location
|
||||
get_docker_configuration_file
|
||||
|
||||
# List all running containers
|
||||
containers=$(docker ps | sed '1d' | awk '{print $NF}')
|
||||
# If there is a container with label docker_bench_security, memorize it:
|
||||
benchcont="nil"
|
||||
for c in $(docker ps | sed '1d' | awk '{print $NF}'); do
|
||||
if docker inspect --format '{{ .Config.Labels }}' "$c" | \
|
||||
grep -e 'docker.bench.security' >/dev/null 2>&1; then
|
||||
benchcont="$c"
|
||||
fi
|
||||
for c in $containers; do
|
||||
labels=$(docker inspect --format '{{ .Config.Labels }}' "$c")
|
||||
contains "$labels" "docker_bench_security" && benchcont="$c"
|
||||
done
|
||||
# List all running containers except docker-bench (use names to improve readability in logs)
|
||||
containers=$(docker ps | sed '1d' | awk '{print $NF}' | grep -v "$benchcont")
|
||||
|
||||
# Get the image id of the docker_bench_security_image, memorize it:
|
||||
benchimagecont="nil"
|
||||
for c in $(docker images | sed '1d' | awk '{print $3}'); do
|
||||
if docker inspect --format '{{ .Config.Labels }}' "$c" | \
|
||||
grep -e 'docker.bench.security' >/dev/null 2>&1; then
|
||||
benchimagecont="$c"
|
||||
fi
|
||||
for test in tests/*.sh
|
||||
do
|
||||
. ./"$test"
|
||||
done
|
||||
|
||||
# Format LABELS
|
||||
for label in $(echo "$labels" | sed 's/,/ /g'); do
|
||||
LABELS="$LABELS --filter label=$label"
|
||||
done
|
||||
|
||||
if [ -n "$include" ]; then
|
||||
pattern=$(echo "$include" | sed 's/,/|/g')
|
||||
containers=$(docker ps $LABELS| sed '1d' | awk '{print $NF}' | grep -v "$benchcont" | grep -E "$pattern")
|
||||
images=$(docker images $LABELS| sed '1d' | grep -E "$pattern" | awk '{print $3}' | grep -v "$benchimagecont")
|
||||
elif [ -n "$exclude" ]; then
|
||||
pattern=$(echo "$exclude" | sed 's/,/|/g')
|
||||
containers=$(docker ps $LABELS| sed '1d' | awk '{print $NF}' | grep -v "$benchcont" | grep -Ev "$pattern")
|
||||
images=$(docker images $LABELS| sed '1d' | grep -Ev "$pattern" | awk '{print $3}' | grep -v "$benchimagecont")
|
||||
else
|
||||
containers=$(docker ps $LABELS| sed '1d' | awk '{print $NF}' | grep -v "$benchcont")
|
||||
images=$(docker images -q $LABELS| grep -v "$benchcont")
|
||||
fi
|
||||
|
||||
for test in $LIBEXEC/tests/*.sh; do
|
||||
. "$test"
|
||||
done
|
||||
|
||||
if [ -z "$check" ] && [ ! "$checkexclude" ]; then
|
||||
# No options just run
|
||||
cis
|
||||
elif [ -z "$check" ]; then
|
||||
# No check defined but excludes defined set to calls in cis() function
|
||||
check=$(sed -ne "/cis() {/,/}/{/{/d; /}/d; p;}" functions/functions_lib.sh)
|
||||
fi
|
||||
|
||||
for c in $(echo "$check" | sed "s/,/ /g"); do
|
||||
if ! command -v "$c" 2>/dev/null 1>&2; then
|
||||
echo "Check \"$c\" doesn't seem to exist."
|
||||
continue
|
||||
fi
|
||||
if [ -z "$checkexclude" ]; then
|
||||
# No excludes just run the checks specified
|
||||
"$c"
|
||||
else
|
||||
# Exludes specified and check exists
|
||||
checkexcluded="$(echo ",$checkexclude" | sed -e 's/^/\^/g' -e 's/,/\$|/g' -e 's/$/\$/g')"
|
||||
|
||||
if echo "$c" | grep -E "$checkexcluded" 2>/dev/null 1>&2; then
|
||||
# Excluded
|
||||
continue
|
||||
elif echo "$c" | grep -vE 'check_[0-9]|check_[a-z]' 2>/dev/null 1>&2; then
|
||||
# Function not a check, fill loop_checks with all check from function
|
||||
loop_checks="$(sed -ne "/$c() {/,/}/{/{/d; /}/d; p;}" functions/functions_lib.sh)"
|
||||
else
|
||||
# Just one check
|
||||
loop_checks="$c"
|
||||
fi
|
||||
|
||||
for lc in $loop_checks; do
|
||||
if echo "$lc" | grep -vE "$checkexcluded" 2>/dev/null 1>&2; then
|
||||
# Not excluded
|
||||
"$lc"
|
||||
fi
|
||||
done
|
||||
fi
|
||||
done
|
||||
|
||||
if [ -n "${globalRemediation}" ] && [ "$printremediation" = "1" ]; then
|
||||
logit "\n\n${bldylw}Section B - Remediation measures${txtrst}"
|
||||
logit "${globalRemediation}"
|
||||
fi
|
||||
|
||||
logit "\n\n${bldylw}Section C - Score${txtrst}\n"
|
||||
info "Checks: $totalChecks"
|
||||
info "Score: $currentScore\n"
|
||||
|
||||
endjson "$totalChecks" "$currentScore" "$(date +%s)"
|
||||
}
|
||||
|
||||
main "$@"
|
||||
|
|
|
|||
|
|
@ -1,21 +1,21 @@
|
|||
services:
|
||||
docker-bench-security:
|
||||
# use image if you have a dedicated build step:
|
||||
# docker build --rm -t docker-bench-security .
|
||||
# image: docker-bench-security
|
||||
docker-bench-security:
|
||||
# use image if you have a dedicated build step:
|
||||
# docker build --rm -t docker-bench-security .
|
||||
# image: docker-bench-security
|
||||
|
||||
# use build path to Dockerfile if docker-compose should build the image
|
||||
build: .
|
||||
# use build path to Dockerfile if docker-compose should build the image
|
||||
build: .
|
||||
|
||||
cap_add:
|
||||
- audit_control
|
||||
labels:
|
||||
- docker_bench_security
|
||||
pid: host
|
||||
stdin_open: true
|
||||
tty: true
|
||||
volumes:
|
||||
- /var/lib:/var/lib:ro
|
||||
- /var/run/docker.sock:/var/run/docker.sock:ro
|
||||
- /usr/lib/systemd:/usr/lib/systemd:ro
|
||||
- /etc:/etc:ro
|
||||
cap_add:
|
||||
- audit_control
|
||||
labels:
|
||||
- docker_bench_security
|
||||
net: host
|
||||
pid: host
|
||||
stdin_open: true
|
||||
tty: true
|
||||
volumes:
|
||||
- /var/lib:/var/lib
|
||||
- /var/run/docker.sock:/var/run/docker.sock
|
||||
- /usr/lib/systemd:/usr/lib/systemd
|
||||
- /etc:/etc
|
||||
|
|
|
|||
|
|
@ -1,571 +0,0 @@
|
|||
#!/bin/sh
|
||||
|
||||
host_configuration() {
|
||||
check_1
|
||||
check_1_1
|
||||
check_1_1_1
|
||||
check_1_1_2
|
||||
check_1_1_3
|
||||
check_1_1_4
|
||||
check_1_1_5
|
||||
check_1_1_6
|
||||
check_1_1_7
|
||||
check_1_1_8
|
||||
check_1_1_9
|
||||
check_1_1_10
|
||||
check_1_1_11
|
||||
check_1_1_12
|
||||
check_1_1_13
|
||||
check_1_1_14
|
||||
check_1_1_15
|
||||
check_1_1_16
|
||||
check_1_1_17
|
||||
check_1_1_18
|
||||
check_1_2
|
||||
check_1_2_1
|
||||
check_1_2_2
|
||||
check_1_end
|
||||
}
|
||||
|
||||
host_configuration_level1() {
|
||||
check_1
|
||||
check_1_end
|
||||
}
|
||||
|
||||
linux_hosts_specific_configuration() {
|
||||
check_1_1
|
||||
check_1_1_1
|
||||
check_1_1_2
|
||||
check_1_1_3
|
||||
check_1_1_4
|
||||
check_1_1_5
|
||||
check_1_1_6
|
||||
check_1_1_7
|
||||
check_1_1_8
|
||||
check_1_1_9
|
||||
check_1_1_10
|
||||
check_1_1_11
|
||||
check_1_1_12
|
||||
check_1_1_13
|
||||
check_1_1_14
|
||||
check_1_1_15
|
||||
check_1_1_16
|
||||
check_1_1_17
|
||||
check_1_1_18
|
||||
}
|
||||
|
||||
host_general_configuration() {
|
||||
check_1
|
||||
check_1_2
|
||||
check_1_2_1
|
||||
check_1_2_2
|
||||
check_1_end
|
||||
}
|
||||
|
||||
docker_daemon_configuration() {
|
||||
check_2
|
||||
check_2_1
|
||||
check_2_2
|
||||
check_2_3
|
||||
check_2_4
|
||||
check_2_5
|
||||
check_2_6
|
||||
check_2_7
|
||||
check_2_8
|
||||
check_2_9
|
||||
check_2_10
|
||||
check_2_11
|
||||
check_2_12
|
||||
check_2_13
|
||||
check_2_14
|
||||
check_2_15
|
||||
check_2_16
|
||||
check_2_17
|
||||
check_2_18
|
||||
check_2_end
|
||||
}
|
||||
|
||||
docker_daemon_configuration_level1() {
|
||||
check_2
|
||||
check_2_end
|
||||
}
|
||||
|
||||
docker_daemon_files() {
|
||||
check_3
|
||||
check_3_1
|
||||
check_3_2
|
||||
check_3_3
|
||||
check_3_4
|
||||
check_3_5
|
||||
check_3_6
|
||||
check_3_7
|
||||
check_3_8
|
||||
check_3_9
|
||||
check_3_10
|
||||
check_3_11
|
||||
check_3_12
|
||||
check_3_13
|
||||
check_3_14
|
||||
check_3_15
|
||||
check_3_16
|
||||
check_3_17
|
||||
check_3_18
|
||||
check_3_19
|
||||
check_3_20
|
||||
check_3_21
|
||||
check_3_22
|
||||
check_3_23
|
||||
check_3_24
|
||||
check_3_end
|
||||
}
|
||||
|
||||
docker_daemon_files_level1() {
|
||||
check_3
|
||||
check_3_end
|
||||
}
|
||||
|
||||
container_images() {
|
||||
check_4
|
||||
check_4_1
|
||||
check_4_2
|
||||
check_4_3
|
||||
check_4_4
|
||||
check_4_5
|
||||
check_4_6
|
||||
check_4_7
|
||||
check_4_8
|
||||
check_4_9
|
||||
check_4_10
|
||||
check_4_11
|
||||
check_4_12
|
||||
check_4_end
|
||||
}
|
||||
|
||||
container_images_level1() {
|
||||
check_4
|
||||
check_4_end
|
||||
}
|
||||
|
||||
container_runtime() {
|
||||
check_5
|
||||
check_running_containers
|
||||
check_5_1
|
||||
check_5_2
|
||||
check_5_3
|
||||
check_5_4
|
||||
check_5_5
|
||||
check_5_6
|
||||
check_5_7
|
||||
check_5_8
|
||||
check_5_9
|
||||
check_5_10
|
||||
check_5_11
|
||||
check_5_12
|
||||
check_5_13
|
||||
check_5_14
|
||||
check_5_15
|
||||
check_5_16
|
||||
check_5_17
|
||||
check_5_18
|
||||
check_5_19
|
||||
check_5_20
|
||||
check_5_21
|
||||
check_5_22
|
||||
check_5_23
|
||||
check_5_24
|
||||
check_5_25
|
||||
check_5_26
|
||||
check_5_27
|
||||
check_5_28
|
||||
check_5_29
|
||||
check_5_30
|
||||
check_5_31
|
||||
check_5_32
|
||||
check_5_end
|
||||
}
|
||||
|
||||
container_runtime_level1() {
|
||||
check_5
|
||||
check_5_end
|
||||
}
|
||||
|
||||
docker_security_operations() {
|
||||
check_6
|
||||
check_6_1
|
||||
check_6_2
|
||||
check_6_end
|
||||
}
|
||||
|
||||
docker_security_operations_level1() {
|
||||
check_6
|
||||
check_6_1
|
||||
check_6_2
|
||||
check_6_end
|
||||
}
|
||||
|
||||
docker_swarm_configuration() {
|
||||
check_7
|
||||
check_7_1
|
||||
check_7_2
|
||||
check_7_3
|
||||
check_7_4
|
||||
check_7_5
|
||||
check_7_6
|
||||
check_7_7
|
||||
check_7_8
|
||||
check_7_9
|
||||
check_7_end
|
||||
}
|
||||
|
||||
docker_swarm_configuration_level1() {
|
||||
check_7
|
||||
check_7_end
|
||||
}
|
||||
|
||||
docker_enterprise_configuration() {
|
||||
check_8
|
||||
check_product_license
|
||||
check_8_1
|
||||
check_8_1_1
|
||||
check_8_1_2
|
||||
check_8_1_3
|
||||
check_8_1_4
|
||||
check_8_1_5
|
||||
check_8_1_6
|
||||
check_8_1_7
|
||||
check_8_2
|
||||
check_8_2_1
|
||||
check_8_end
|
||||
}
|
||||
|
||||
docker_enterprise_configuration_level1() {
|
||||
check_8
|
||||
check_product_license
|
||||
check_8_1
|
||||
check_8_1_1
|
||||
check_8_1_2
|
||||
check_8_1_3
|
||||
check_8_1_4
|
||||
check_8_1_5
|
||||
check_8_1_6
|
||||
check_8_1_7
|
||||
check_8_2
|
||||
check_8_2_1
|
||||
check_8_end
|
||||
}
|
||||
|
||||
universal_control_plane_configuration() {
|
||||
check_8
|
||||
check_8_1
|
||||
check_8_1_1
|
||||
check_8_1_2
|
||||
check_8_1_3
|
||||
check_8_1_4
|
||||
check_8_1_5
|
||||
check_8_1_6
|
||||
check_8_1_7
|
||||
check_8_end
|
||||
}
|
||||
|
||||
docker_trusted_registry_configuration() {
|
||||
check_8
|
||||
check_8_2
|
||||
check_8_2_1
|
||||
check_8_end
|
||||
}
|
||||
|
||||
community_checks() {
|
||||
check_c
|
||||
check_c_1
|
||||
check_c_1_1
|
||||
check_c_2
|
||||
check_c_5_3_1
|
||||
check_c_5_3_2
|
||||
check_c_5_3_3
|
||||
check_c_5_3_4
|
||||
check_c_end
|
||||
}
|
||||
|
||||
# CIS
|
||||
cis() {
|
||||
host_configuration
|
||||
docker_daemon_configuration
|
||||
docker_daemon_files
|
||||
container_images
|
||||
container_runtime
|
||||
docker_security_operations
|
||||
docker_swarm_configuration
|
||||
}
|
||||
|
||||
cis_level1() {
|
||||
host_configuration_level1
|
||||
docker_daemon_configuration_level1
|
||||
docker_daemon_files_level1
|
||||
container_images_level1
|
||||
container_runtime_level1
|
||||
docker_security_operations_level1
|
||||
docker_swarm_configuration_level1
|
||||
}
|
||||
|
||||
cis_controls_v8_ig1() {
|
||||
check_1_1_2
|
||||
check_1_1_3
|
||||
check_2_1
|
||||
check_2_13
|
||||
check_2_14
|
||||
check_3_1
|
||||
check_3_2
|
||||
check_3_3
|
||||
check_3_4
|
||||
check_3_5
|
||||
check_3_6
|
||||
check_3_7
|
||||
check_3_8
|
||||
check_3_9
|
||||
check_3_10
|
||||
check_3_11
|
||||
check_3_12
|
||||
check_3_13
|
||||
check_3_14
|
||||
check_3_15
|
||||
check_3_16
|
||||
check_3_17
|
||||
check_3_18
|
||||
check_3_19
|
||||
check_3_20
|
||||
check_3_21
|
||||
check_3_22
|
||||
check_3_23
|
||||
check_3_24
|
||||
check_4_8
|
||||
check_4_11
|
||||
check_5_5
|
||||
check_5_14
|
||||
check_5_18
|
||||
check_5_22
|
||||
check_5_23
|
||||
check_5_24
|
||||
check_5_25
|
||||
check_5_26
|
||||
check_5_32
|
||||
check_7_2
|
||||
check_7_6
|
||||
check_7_7
|
||||
check_7_8
|
||||
}
|
||||
|
||||
cis_controls_v8_ig2() {
|
||||
check_1_1_1
|
||||
check_1_1_2
|
||||
check_1_1_3
|
||||
check_1_1_4
|
||||
check_1_1_5
|
||||
check_1_1_6
|
||||
check_1_1_7
|
||||
check_1_1_8
|
||||
check_1_1_9
|
||||
check_1_1_10
|
||||
check_1_1_11
|
||||
check_1_1_12
|
||||
check_1_1_13
|
||||
check_1_1_14
|
||||
check_1_1_15
|
||||
check_1_1_16
|
||||
check_1_1_17
|
||||
check_1_1_18
|
||||
check_1_2_1
|
||||
check_1_2_2
|
||||
check_2_1
|
||||
check_2_2
|
||||
check_2_3
|
||||
check_2_4
|
||||
check_2_5
|
||||
check_2_7
|
||||
check_2_8
|
||||
check_2_11
|
||||
check_2_13
|
||||
check_2_14
|
||||
check_2_15
|
||||
check_2_16
|
||||
check_2_18
|
||||
check_3_1
|
||||
check_3_2
|
||||
check_3_3
|
||||
check_3_4
|
||||
check_3_5
|
||||
check_3_6
|
||||
check_3_7
|
||||
check_3_8
|
||||
check_3_9
|
||||
check_3_10
|
||||
check_3_11
|
||||
check_3_12
|
||||
check_3_13
|
||||
check_3_14
|
||||
check_3_15
|
||||
check_3_16
|
||||
check_3_17
|
||||
check_3_18
|
||||
check_3_19
|
||||
check_3_20
|
||||
check_3_21
|
||||
check_3_22
|
||||
check_3_23
|
||||
check_3_24
|
||||
check_4_2
|
||||
check_4_3
|
||||
check_4_4
|
||||
check_4_7
|
||||
check_4_8
|
||||
check_4_9
|
||||
check_4_11
|
||||
check_5_1
|
||||
check_5_2
|
||||
check_5_3
|
||||
check_5_4
|
||||
check_5_5
|
||||
check_5_7
|
||||
check_5_10
|
||||
check_5_11
|
||||
check_5_12
|
||||
check_5_14
|
||||
check_5_16
|
||||
check_5_17
|
||||
check_5_18
|
||||
check_5_19
|
||||
check_5_21
|
||||
check_5_22
|
||||
check_5_23
|
||||
check_5_24
|
||||
check_5_25
|
||||
check_5_26
|
||||
check_5_27
|
||||
check_5_30
|
||||
check_5_31
|
||||
check_5_32
|
||||
check_6_1
|
||||
check_6_2
|
||||
check_7_2
|
||||
check_7_3
|
||||
check_7_5
|
||||
check_7_6
|
||||
check_7_7
|
||||
check_7_8
|
||||
check_7_9
|
||||
}
|
||||
|
||||
cis_controls_v8_ig3() {
|
||||
check_1_1_1
|
||||
check_1_1_2
|
||||
check_1_1_3
|
||||
check_1_1_4
|
||||
check_1_1_5
|
||||
check_1_1_6
|
||||
check_1_1_7
|
||||
check_1_1_8
|
||||
check_1_1_9
|
||||
check_1_1_10
|
||||
check_1_1_11
|
||||
check_1_1_12
|
||||
check_1_1_13
|
||||
check_1_1_14
|
||||
check_1_1_15
|
||||
check_1_1_16
|
||||
check_1_1_17
|
||||
check_1_1_18
|
||||
check_1_2_1
|
||||
check_1_2_2
|
||||
check_2_1
|
||||
check_2_2
|
||||
check_2_3
|
||||
check_2_4
|
||||
check_2_5
|
||||
check_2_7
|
||||
check_2_8
|
||||
check_2_11
|
||||
check_2_13
|
||||
check_2_14
|
||||
check_2_15
|
||||
check_2_16
|
||||
check_2_18
|
||||
check_3_1
|
||||
check_3_2
|
||||
check_3_3
|
||||
check_3_4
|
||||
check_3_5
|
||||
check_3_6
|
||||
check_3_7
|
||||
check_3_8
|
||||
check_3_9
|
||||
check_3_10
|
||||
check_3_11
|
||||
check_3_12
|
||||
check_3_13
|
||||
check_3_14
|
||||
check_3_15
|
||||
check_3_16
|
||||
check_3_17
|
||||
check_3_18
|
||||
check_3_19
|
||||
check_3_20
|
||||
check_3_21
|
||||
check_3_22
|
||||
check_3_23
|
||||
check_3_24
|
||||
check_4_2
|
||||
check_4_3
|
||||
check_4_4
|
||||
check_4_6
|
||||
check_4_7
|
||||
check_4_8
|
||||
check_4_9
|
||||
check_4_11
|
||||
check_4_12
|
||||
check_5_1
|
||||
check_5_2
|
||||
check_5_3
|
||||
check_5_4
|
||||
check_5_5
|
||||
check_5_7
|
||||
check_5_8
|
||||
check_5_9
|
||||
check_5_10
|
||||
check_5_11
|
||||
check_5_12
|
||||
check_5_14
|
||||
check_5_16
|
||||
check_5_17
|
||||
check_5_18
|
||||
check_5_19
|
||||
check_5_21
|
||||
check_5_22
|
||||
check_5_23
|
||||
check_5_24
|
||||
check_5_25
|
||||
check_5_26
|
||||
check_5_27
|
||||
check_5_30
|
||||
check_5_31
|
||||
check_5_32
|
||||
check_6_1
|
||||
check_6_2
|
||||
check_7_2
|
||||
check_7_3
|
||||
check_7_5
|
||||
check_7_6
|
||||
check_7_7
|
||||
check_7_8
|
||||
check_7_9
|
||||
}
|
||||
|
||||
# Community contributed
|
||||
community() {
|
||||
community_checks
|
||||
}
|
||||
|
||||
# All
|
||||
all() {
|
||||
cis
|
||||
docker_enterprise_configuration
|
||||
community
|
||||
}
|
||||
|
|
@ -1,163 +0,0 @@
|
|||
#!/bin/bash
|
||||
|
||||
# Returns the absolute path of a given string
|
||||
abspath () { case "$1" in /*)printf "%s\n" "$1";; *)printf "%s\n" "$PWD/$1";; esac; }
|
||||
|
||||
# Audit rules default path
|
||||
auditrules="/etc/audit/audit.rules"
|
||||
|
||||
# Check for required program(s)
|
||||
req_programs() {
|
||||
for p in $1; do
|
||||
command -v "$p" >/dev/null 2>&1 || { printf "Required program not found: %s\n" "$p"; exit 1; }
|
||||
done
|
||||
if command -v jq >/dev/null 2>&1; then
|
||||
HAVE_JQ=true
|
||||
else
|
||||
HAVE_JQ=false
|
||||
fi
|
||||
if command -v ss >/dev/null 2>&1; then
|
||||
netbin=ss
|
||||
return
|
||||
fi
|
||||
if command -v netstat >/dev/null 2>&1; then
|
||||
netbin=netstat
|
||||
return
|
||||
fi
|
||||
echo "ss or netstat command not found."
|
||||
exit 1
|
||||
}
|
||||
|
||||
# Compares versions of software of the format X.Y.Z
|
||||
do_version_check() {
|
||||
[ "$1" = "$2" ] && return 10
|
||||
|
||||
ver1front=$(printf "%s" "$1" | cut -d "." -f -1)
|
||||
ver1back=$(printf "%s" "$1" | cut -d "." -f 2-)
|
||||
ver2front=$(printf "%s" "$2" | cut -d "." -f -1)
|
||||
ver2back=$(printf "%s" "$2" | cut -d "." -f 2-)
|
||||
|
||||
if [ "$ver1front" != "$1" ] || [ "$ver2front" != "$2" ]; then
|
||||
[ "$ver1front" -gt "$ver2front" ] && return 11
|
||||
[ "$ver1front" -lt "$ver2front" ] && return 9
|
||||
|
||||
[ "$ver1front" = "$1" ] || [ -z "$ver1back" ] && ver1back=0
|
||||
[ "$ver2front" = "$2" ] || [ -z "$ver2back" ] && ver2back=0
|
||||
do_version_check "$ver1back" "$ver2back"
|
||||
return $?
|
||||
fi
|
||||
[ "$1" -gt "$2" ] && return 11 || return 9
|
||||
}
|
||||
|
||||
# Extracts commandline args from the newest running processes named like the first parameter
|
||||
get_command_line_args() {
|
||||
PROC="$1"
|
||||
|
||||
for PID in $(pgrep -f -n "$PROC"); do
|
||||
tr "\0" " " < /proc/"$PID"/cmdline
|
||||
done
|
||||
}
|
||||
|
||||
# Extract the cumulative command line arguments for the docker daemon
|
||||
#
|
||||
# If specified multiple times, all matches are returned.
|
||||
# Accounts for long and short variants, call with short option.
|
||||
# Does not account for option defaults or implicit options.
|
||||
get_docker_cumulative_command_line_args() {
|
||||
OPTION="$1"
|
||||
|
||||
line_arg="dockerd"
|
||||
if ! get_command_line_args "docker daemon" >/dev/null 2>&1 ; then
|
||||
line_arg="docker daemon"
|
||||
fi
|
||||
|
||||
get_command_line_args "$line_arg" |
|
||||
# normalize known long options to their short versions
|
||||
sed \
|
||||
-e 's/\-\-debug/-D/g' \
|
||||
-e 's/\-\-host/-H/g' \
|
||||
-e 's/\-\-log-level/-l/g' \
|
||||
-e 's/\-\-version/-v/g' \
|
||||
|
|
||||
# normalize parameters separated by space(s) to -O=VALUE
|
||||
sed \
|
||||
-e 's/\-\([DHlv]\)[= ]\([^- ][^ ]\)/-\1=\2/g' \
|
||||
|
|
||||
# get the last interesting option
|
||||
tr ' ' "\n" |
|
||||
grep "^${OPTION}" |
|
||||
# normalize quoting of values
|
||||
sed \
|
||||
-e 's/"//g' \
|
||||
-e "s/'//g"
|
||||
}
|
||||
|
||||
# Extract the effective command line arguments for the docker daemon
|
||||
#
|
||||
# Accounts for multiple specifications, takes the last option.
|
||||
# Accounts for long and short variants, call with short option
|
||||
# Does not account for option default or implicit options.
|
||||
get_docker_effective_command_line_args() {
|
||||
OPTION="$1"
|
||||
get_docker_cumulative_command_line_args "$OPTION" | tail -n1
|
||||
}
|
||||
|
||||
get_docker_configuration_file() {
|
||||
FILE="$(get_docker_effective_command_line_args '--config-file' | \
|
||||
sed 's/.*=//g')"
|
||||
|
||||
if [ -f "$FILE" ]; then
|
||||
CONFIG_FILE="$FILE"
|
||||
return
|
||||
fi
|
||||
if [ -f '/etc/docker/daemon.json' ]; then
|
||||
CONFIG_FILE='/etc/docker/daemon.json'
|
||||
return
|
||||
fi
|
||||
CONFIG_FILE='/dev/null'
|
||||
}
|
||||
|
||||
get_docker_configuration_file_args() {
|
||||
OPTION="$1"
|
||||
|
||||
get_docker_configuration_file
|
||||
|
||||
if "$HAVE_JQ"; then
|
||||
jq --monochrome-output --raw-output "if has(\"${OPTION}\") then .[\"${OPTION}\"] else \"\" end" "$CONFIG_FILE"
|
||||
else
|
||||
cat "$CONFIG_FILE" | tr , '\n' | grep "$OPTION" | sed 's/.*://g' | tr -d '" ',
|
||||
fi
|
||||
}
|
||||
|
||||
get_service_file() {
|
||||
SERVICE="$1"
|
||||
|
||||
if [ -f "/etc/systemd/system/$SERVICE" ]; then
|
||||
echo "/etc/systemd/system/$SERVICE"
|
||||
return
|
||||
fi
|
||||
if [ -f "/lib/systemd/system/$SERVICE" ]; then
|
||||
echo "/lib/systemd/system/$SERVICE"
|
||||
return
|
||||
fi
|
||||
if find /run -name "$SERVICE" 2> /dev/null 1>&2; then
|
||||
find /run -name "$SERVICE" | head -n1
|
||||
return
|
||||
fi
|
||||
if [ "$(systemctl show -p FragmentPath "$SERVICE" | sed 's/.*=//')" != "" ]; then
|
||||
systemctl show -p FragmentPath "$SERVICE" | sed 's/.*=//'
|
||||
return
|
||||
fi
|
||||
echo "/usr/lib/systemd/system/$SERVICE"
|
||||
}
|
||||
|
||||
yell_info() {
|
||||
yell "# --------------------------------------------------------------------------------------------
|
||||
# Docker Bench for Security v$version
|
||||
#
|
||||
# Docker, Inc. (c) 2015-$(date +"%Y")
|
||||
#
|
||||
# Checks for dozens of common best-practices around deploying Docker containers in production.
|
||||
# Based on the CIS Docker Benchmark 1.6.0.
|
||||
# --------------------------------------------------------------------------------------------"
|
||||
}
|
||||
|
|
@ -1,190 +0,0 @@
|
|||
#!/bin/bash
|
||||
|
||||
bldred='\033[1;31m' # Bold Red
|
||||
bldgrn='\033[1;32m' # Bold Green
|
||||
bldblu='\033[1;34m' # Bold Blue
|
||||
bldylw='\033[1;33m' # Bold Yellow
|
||||
txtrst='\033[0m'
|
||||
|
||||
if [ -n "$nocolor" ] && [ "$nocolor" = "nocolor" ]; then
|
||||
bldred=''
|
||||
bldgrn=''
|
||||
bldblu=''
|
||||
bldylw=''
|
||||
txtrst=''
|
||||
fi
|
||||
|
||||
logit () {
|
||||
printf "%b\n" "$1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
info () {
|
||||
local infoCountCheck
|
||||
local OPTIND c
|
||||
while getopts c args
|
||||
do
|
||||
case $args in
|
||||
c) infoCountCheck="true" ;;
|
||||
*) exit 1 ;;
|
||||
esac
|
||||
done
|
||||
if [ "$infoCountCheck" = "true" ]; then
|
||||
printf "%b\n" "${bldblu}[INFO]${txtrst} $2" | tee -a "$logger"
|
||||
totalChecks=$((totalChecks + 1))
|
||||
return
|
||||
fi
|
||||
printf "%b\n" "${bldblu}[INFO]${txtrst} $1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
pass () {
|
||||
local passScored
|
||||
local passCountCheck
|
||||
local OPTIND s c
|
||||
while getopts sc args
|
||||
do
|
||||
case $args in
|
||||
s) passScored="true" ;;
|
||||
c) passCountCheck="true" ;;
|
||||
*) exit 1 ;;
|
||||
esac
|
||||
done
|
||||
if [ "$passScored" = "true" ] || [ "$passCountCheck" = "true" ]; then
|
||||
printf "%b\n" "${bldgrn}[PASS]${txtrst} $2" | tee -a "$logger"
|
||||
totalChecks=$((totalChecks + 1))
|
||||
fi
|
||||
if [ "$passScored" = "true" ]; then
|
||||
currentScore=$((currentScore + 1))
|
||||
fi
|
||||
if [ "$passScored" != "true" ] && [ "$passCountCheck" != "true" ]; then
|
||||
printf "%b\n" "${bldgrn}[PASS]${txtrst} $1" | tee -a "$logger"
|
||||
fi
|
||||
}
|
||||
|
||||
warn () {
|
||||
local warnScored
|
||||
local OPTIND s
|
||||
while getopts s args
|
||||
do
|
||||
case $args in
|
||||
s) warnScored="true" ;;
|
||||
*) exit 1 ;;
|
||||
esac
|
||||
done
|
||||
if [ "$warnScored" = "true" ]; then
|
||||
printf "%b\n" "${bldred}[WARN]${txtrst} $2" | tee -a "$logger"
|
||||
totalChecks=$((totalChecks + 1))
|
||||
currentScore=$((currentScore - 1))
|
||||
return
|
||||
fi
|
||||
printf "%b\n" "${bldred}[WARN]${txtrst} $1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
note () {
|
||||
local noteCountCheck
|
||||
local OPTIND c
|
||||
while getopts c args
|
||||
do
|
||||
case $args in
|
||||
c) noteCountCheck="true" ;;
|
||||
*) exit 1 ;;
|
||||
esac
|
||||
done
|
||||
if [ "$noteCountCheck" = "true" ]; then
|
||||
printf "%b\n" "${bldylw}[NOTE]${txtrst} $2" | tee -a "$logger"
|
||||
totalChecks=$((totalChecks + 1))
|
||||
return
|
||||
fi
|
||||
printf "%b\n" "${bldylw}[NOTE]${txtrst} $1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
yell () {
|
||||
printf "%b\n" "${bldylw}$1${txtrst}\n"
|
||||
}
|
||||
|
||||
beginjson () {
|
||||
printf "{\n \"dockerbenchsecurity\": \"%s\",\n \"start\": %s,\n \"tests\": [" "$1" "$2" | tee "$logger.json" 2>/dev/null 1>&2
|
||||
}
|
||||
|
||||
endjson (){
|
||||
printf "\n ],\n \"checks\": %s,\n \"score\": %s,\n \"end\": %s\n}" "$1" "$2" "$3" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
}
|
||||
|
||||
logjson (){
|
||||
printf "\n \"%s\": \"%s\"," "$1" "$2" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
}
|
||||
|
||||
SSEP=
|
||||
SEP=
|
||||
startsectionjson() {
|
||||
printf "%s\n {\n \"id\": \"%s\",\n \"desc\": \"%s\",\n \"results\": [" "$SSEP" "$1" "$2" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
SEP=
|
||||
SSEP=","
|
||||
}
|
||||
|
||||
endsectionjson() {
|
||||
printf "\n ]\n }" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
}
|
||||
|
||||
starttestjson() {
|
||||
printf "%s\n {\n \"id\": \"%s\",\n \"desc\": \"%s\",\n " "$SEP" "$1" "$2" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
SEP=","
|
||||
}
|
||||
|
||||
log_to_json() {
|
||||
if [ $# -eq 1 ]; then
|
||||
printf "\"result\": \"%s\"" "$1" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
return
|
||||
fi
|
||||
if [ $# -eq 2 ] && [ $# -ne 1 ]; then
|
||||
# Result also contains details
|
||||
printf "\"result\": \"%s\",\n \"details\": \"%s\"" "$1" "$2" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
return
|
||||
fi
|
||||
# Result also includes details and a list of items. Add that directly to details and to an array property "items"
|
||||
# Also limit the number of items to $limit, if $limit is non-zero
|
||||
truncItems=$3
|
||||
if [ "$limit" != 0 ]; then
|
||||
truncItems=""
|
||||
ITEM_COUNT=0
|
||||
for item in $3; do
|
||||
truncItems="$truncItems $item"
|
||||
ITEM_COUNT=$((ITEM_COUNT + 1));
|
||||
if [ "$ITEM_COUNT" == "$limit" ]; then
|
||||
truncItems="$truncItems (truncated)"
|
||||
break;
|
||||
fi
|
||||
done
|
||||
fi
|
||||
itemsJson=$(printf "[\n "; ISEP=""; ITEMCOUNT=0; for item in $truncItems; do printf "%s\"%s\"" "$ISEP" "$item"; ISEP=","; done; printf "\n ]")
|
||||
printf "\"result\": \"%s\",\n \"details\": \"%s: %s\",\n \"items\": %s" "$1" "$2" "$truncItems" "$itemsJson" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
}
|
||||
|
||||
logcheckresult() {
|
||||
# Log to JSON
|
||||
log_to_json "$@"
|
||||
|
||||
# Log remediation measure to JSON
|
||||
if [ -n "$remediation" ] && [ "$1" != "PASS" ] && [ "$printremediation" = "1" ]; then
|
||||
printf ",\n \"remediation\": \"%s\"" "$remediation" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
if [ -n "$remediationImpact" ]; then
|
||||
printf ",\n \"remediation-impact\": \"%s\"" "$remediationImpact" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
fi
|
||||
fi
|
||||
printf "\n }" | tee -a "$logger.json" 2>/dev/null 1>&2
|
||||
|
||||
# Save remediation measure for print log to stdout
|
||||
if [ -n "$remediation" ] && [ "$1" != "PASS" ]; then
|
||||
if [ -n "${checkHeader}" ]; then
|
||||
if [ -n "${addSpaceHeader}" ]; then
|
||||
globalRemediation="${globalRemediation}\n"
|
||||
fi
|
||||
globalRemediation="${globalRemediation}\n${bldblu}[INFO]${txtrst} ${checkHeader}"
|
||||
checkHeader=""
|
||||
addSpaceHeader="1"
|
||||
fi
|
||||
globalRemediation="${globalRemediation}\n${bldblu}[INFO]${txtrst} ${id} - ${remediation}"
|
||||
if [ -n "${remediationImpact}" ]; then
|
||||
globalRemediation="${globalRemediation} Remediation Impact: ${remediationImpact}"
|
||||
fi
|
||||
fi
|
||||
}
|
||||
105
helper_lib.sh
Normal file
105
helper_lib.sh
Normal file
|
|
@ -0,0 +1,105 @@
|
|||
#!/bin/sh
|
||||
|
||||
# Returns the absolute path of a given string
|
||||
abspath () { case "$1" in /*)printf "%s\n" "$1";; *)printf "%s\n" "$PWD/$1";; esac; }
|
||||
|
||||
# Compares versions of software of the format X.Y.Z
|
||||
do_version_check() {
|
||||
[ "$1" = "$2" ] && return 10
|
||||
|
||||
ver1front=$(printf "%s" "$1" | cut -d "." -f -1)
|
||||
ver1back=$(printf "%s" "$1" | cut -d "." -f 2-)
|
||||
ver2front=$(printf "%s" "$2" | cut -d "." -f -1)
|
||||
ver2back=$(printf "%s" "$2" | cut -d "." -f 2-)
|
||||
|
||||
if [ "$ver1front" != "$1" ] || [ "$ver2front" != "$2" ]; then
|
||||
[ "$ver1front" -gt "$ver2front" ] && return 11
|
||||
[ "$ver1front" -lt "$ver2front" ] && return 9
|
||||
|
||||
[ "$ver1front" = "$1" ] || [ -z "$ver1back" ] && ver1back=0
|
||||
[ "$ver2front" = "$2" ] || [ -z "$ver2back" ] && ver2back=0
|
||||
do_version_check "$ver1back" "$ver2back"
|
||||
return $?
|
||||
else
|
||||
[ "$1" -gt "$2" ] && return 11 || return 9
|
||||
fi
|
||||
}
|
||||
|
||||
# Compares two strings and returns 0 if the second is a substring of the first
|
||||
contains() {
|
||||
string="$1"
|
||||
substring="$2"
|
||||
if [ "${string#*$substring}" != "$string" ]
|
||||
then
|
||||
return 0 # $substring is in $string
|
||||
else
|
||||
return 1 # $substring is not in $string
|
||||
fi
|
||||
}
|
||||
|
||||
# Extracts commandline args from the newest running processes named like the first parameter
|
||||
get_command_line_args() {
|
||||
PROC="$1"
|
||||
|
||||
for PID in $(pgrep -f -n "$PROC")
|
||||
do
|
||||
tr "\0" " " < /proc/"$PID"/cmdline
|
||||
done
|
||||
}
|
||||
|
||||
# Extract the cumulative command line arguments for the docker daemon
|
||||
#
|
||||
# If specified multiple times, all matches are returned.
|
||||
# Accounts for long and short variants, call with short option.
|
||||
# Does not account for option defaults or implicit options.
|
||||
get_docker_cumulative_command_line_args() {
|
||||
OPTION="$1"
|
||||
|
||||
if ! get_command_line_args "docker daemon" >/dev/null 2>&1 ; then
|
||||
line_arg="docker daemon"
|
||||
else
|
||||
line_arg="dockerd"
|
||||
fi
|
||||
|
||||
get_command_line_args "$line_arg" |
|
||||
# normalize known long options to their short versions
|
||||
sed \
|
||||
-e 's/\-\-debug/-D/g' \
|
||||
-e 's/\-\-host/-H/g' \
|
||||
-e 's/\-\-log-level/-l/g' \
|
||||
-e 's/\-\-version/-v/g' \
|
||||
|
|
||||
# normalize parameters separated by space(s) to -O=VALUE
|
||||
sed \
|
||||
-e 's/\-\([DHlv]\)[= ]\([^- ][^ ]\)/-\1=\2/g' \
|
||||
|
|
||||
# get the last interesting option
|
||||
tr ' ' "\n" |
|
||||
grep "^${OPTION}" |
|
||||
# normalize quoting of values
|
||||
sed \
|
||||
-e 's/"//g' \
|
||||
-e "s/'//g"
|
||||
}
|
||||
|
||||
# Extract the effective command line arguments for the docker daemon
|
||||
#
|
||||
# Accounts for multiple specifications, takes the last option.
|
||||
# Accounts for long and short variants, call with short option
|
||||
# Does not account for option default or implicit options.
|
||||
get_docker_effective_command_line_args() {
|
||||
OPTION="$1"
|
||||
get_docker_cumulative_command_line_args $OPTION | tail -n1
|
||||
}
|
||||
|
||||
get_systemd_service_file(){
|
||||
SERVICE="$1"
|
||||
|
||||
if [ -f "/etc/systemd/system/$SERVICE" ]; then
|
||||
echo "/etc/systemd/system/$SERVICE"
|
||||
elif systemctl show -p FragmentPath "$SERVICE" 2> /dev/null 1>&2; then
|
||||
systemctl show -p FragmentPath "$SERVICE" | sed 's/.*=//'
|
||||
else
|
||||
echo "/usr/lib/systemd/system/$SERVICE"
|
||||
fi
|
||||
}
|
||||
Binary file not shown.
|
Before 
(image error) Size: 346 KiB |
26
output_lib.sh
Normal file
26
output_lib.sh
Normal file
|
|
@ -0,0 +1,26 @@
|
|||
#!/bin/sh
|
||||
bldred='\033[1;31m'
|
||||
bldgrn='\033[1;32m'
|
||||
bldblu='\033[1;34m'
|
||||
bldylw='\033[1;33m' # Yellow
|
||||
txtrst='\033[0m'
|
||||
|
||||
logit () {
|
||||
printf "%b\n" "$1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
info () {
|
||||
printf "%b\n" "${bldblu}[INFO]${txtrst} $1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
pass () {
|
||||
printf "%b\n" "${bldgrn}[PASS]${txtrst} $1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
warn () {
|
||||
printf "%b\n" "${bldred}[WARN]${txtrst} $1" | tee -a "$logger"
|
||||
}
|
||||
|
||||
yell () {
|
||||
printf "%b\n" "${bldylw}$1${txtrst}\n"
|
||||
}
|
||||
|
|
@ -1,662 +1,242 @@
|
|||
#!/bin/bash
|
||||
#!/bin/sh
|
||||
|
||||
check_1() {
|
||||
logit ""
|
||||
local id="1"
|
||||
local desc="Host Configuration"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
logit ""
|
||||
info "1 - Host Configuration"
|
||||
|
||||
check_1_1() {
|
||||
local id="1.1"
|
||||
local desc="Linux Hosts Specific Configuration"
|
||||
local check="$id - $desc"
|
||||
info "$check"
|
||||
}
|
||||
# 1.1
|
||||
check_1_1="1.1 - Create a separate partition for containers"
|
||||
grep /var/lib/docker /etc/fstab >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_1"
|
||||
else
|
||||
warn "$check_1_1"
|
||||
fi
|
||||
|
||||
check_1_1_1() {
|
||||
local id="1.1.1"
|
||||
local desc="Ensure a separate partition for containers has been created (Automated)"
|
||||
local remediation="For new installations, you should create a separate partition for the /var/lib/docker mount point. For systems that have already been installed, you should use the Logical Volume Manager (LVM) within Linux to create a new partition."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 1.2
|
||||
check_1_2="1.2 - Use an updated Linux Kernel"
|
||||
kernel_version=$(uname -r | cut -d "-" -f 1)
|
||||
do_version_check 3.10 "$kernel_version"
|
||||
if [ $? -eq 11 ]; then
|
||||
warn "$check_1_2"
|
||||
else
|
||||
pass "$check_1_2"
|
||||
fi
|
||||
|
||||
docker_root_dir=$(docker info -f '{{ .DockerRootDir }}')
|
||||
if docker info | grep -q userns ; then
|
||||
docker_root_dir=$(readlink -f "$docker_root_dir/..")
|
||||
# 1.3
|
||||
check_1_3="1.3 - Harden the container host"
|
||||
info "$check_1_3"
|
||||
|
||||
# 1.4
|
||||
check_1_4="1.4 - Remove all non-essential services from the host - Network"
|
||||
# Check for listening network services.
|
||||
listening_services=$(netstat -na | grep -v tcp6 | grep -v unix | grep -c LISTEN)
|
||||
if [ "$listening_services" -eq 0 ]; then
|
||||
info "1.4 - Failed to get listening services for check: $check_1_4"
|
||||
else
|
||||
if [ "$listening_services" -gt 5 ]; then
|
||||
info "$check_1_4"
|
||||
info " * Host listening on: $listening_services ports"
|
||||
else
|
||||
pass "$check_1_4"
|
||||
fi
|
||||
fi
|
||||
|
||||
if mountpoint -q -- "$docker_root_dir" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
# 1.5
|
||||
check_1_5="1.5 - Keep Docker up to date"
|
||||
docker_version=$(docker version | grep -i -A1 '^server' | grep -i 'version:' \
|
||||
| awk '{print $NF; exit}' | tr -d '[:alpha:]-,')
|
||||
docker_current_version="1.13.0"
|
||||
docker_current_date="2017-01-18"
|
||||
do_version_check "$docker_current_version" "$docker_version"
|
||||
if [ $? -eq 11 ]; then
|
||||
info "$check_1_5"
|
||||
info " * Using $docker_version, when $docker_current_version is current as of $docker_current_date"
|
||||
info " * Your operating system vendor may provide support and security maintenance for docker"
|
||||
else
|
||||
pass "$check_1_5"
|
||||
info " * Using $docker_version which is current as of $docker_current_date"
|
||||
info " * Check with your operating system vendor for support and security maintenance for docker"
|
||||
fi
|
||||
|
||||
check_1_1_2() {
|
||||
local id="1.1.2"
|
||||
local desc="Ensure only trusted users are allowed to control Docker daemon (Automated)"
|
||||
local remediation="You should remove any untrusted users from the docker group using command sudo gpasswd -d <your-user> docker or add trusted users to the docker group using command sudo usermod -aG docker <your-user>. You should not create a mapping of sensitive directories from the host to container volumes."
|
||||
local remediationImpact="Only trust user are allow to build and execute containers as normal user."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 1.6
|
||||
check_1_6="1.6 - Only allow trusted users to control Docker daemon"
|
||||
docker_users=$(getent group docker)
|
||||
info "$check_1_6"
|
||||
for u in $docker_users; do
|
||||
info " * $u"
|
||||
done
|
||||
|
||||
docker_users=$(grep 'docker' /etc/group)
|
||||
if command -v getent >/dev/null 2>&1; then
|
||||
docker_users=$(getent group docker)
|
||||
fi
|
||||
docker_users=$(printf "%s" "$docker_users" | awk -F: '{print $4}')
|
||||
|
||||
local doubtfulusers=""
|
||||
if [ -n "$dockertrustusers" ]; then
|
||||
for u in $(printf "%s" "$docker_users" | sed "s/,/ /g"); do
|
||||
if ! printf "%s" "$dockertrustusers" | grep -q "$u" ; then
|
||||
doubtfulusers="$u"
|
||||
if [ -n "${doubtfulusers}" ]; then
|
||||
doubtfulusers="${doubtfulusers},$u"
|
||||
fi
|
||||
fi
|
||||
done
|
||||
# 1.7
|
||||
check_1_7="1.7 - Audit docker daemon - /usr/bin/docker"
|
||||
file="/usr/bin/docker"
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep "$file" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_7"
|
||||
else
|
||||
info -c "$check"
|
||||
info " * Users: $docker_users"
|
||||
logcheckresult "INFO" "doubtfulusers" "$docker_users"
|
||||
warn "$check_1_7"
|
||||
fi
|
||||
else
|
||||
warn "1.7 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
|
||||
if [ -n "${doubtfulusers}" ]; then
|
||||
warn -s "$check"
|
||||
warn " * Doubtful users: $doubtfulusers"
|
||||
logcheckresult "WARN" "doubtfulusers" "$doubtfulusers"
|
||||
# 1.8
|
||||
check_1_8="1.8 - Audit Docker files and directories - /var/lib/docker"
|
||||
directory="/var/lib/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep $directory >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_8"
|
||||
else
|
||||
warn "$check_1_8"
|
||||
fi
|
||||
else
|
||||
warn "1.8 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
else
|
||||
info "$check_1_8"
|
||||
info " * Directory not found"
|
||||
fi
|
||||
|
||||
if [ -z "${doubtfulusers}" ] && [ -n "${dockertrustusers}" ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
# 1.9
|
||||
check_1_9="1.9 - Audit Docker files and directories - /etc/docker"
|
||||
directory="/etc/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep $directory >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_9"
|
||||
else
|
||||
warn "$check_1_9"
|
||||
fi
|
||||
else
|
||||
warn "1.9 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
}
|
||||
else
|
||||
info "$check_1_9"
|
||||
info " * Directory not found"
|
||||
fi
|
||||
|
||||
check_1_1_3() {
|
||||
local id="1.1.3"
|
||||
local desc="Ensure auditing is configured for the Docker daemon (Automated)"
|
||||
local remediation="Install auditd. Add -w /usr/bin/dockerd -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/usr/bin/dockerd"
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep "$file" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
# 1.10
|
||||
check_1_10="1.10 - Audit Docker files and directories - docker.service"
|
||||
file="$(get_systemd_service_file docker.service)"
|
||||
if [ -f "$file" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep "$file" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_10"
|
||||
else
|
||||
warn "$check_1_10"
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
else
|
||||
warn "1.10 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
else
|
||||
info "$check_1_10"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
# 1.11
|
||||
check_1_11="1.11 - Audit Docker files and directories - docker.socket"
|
||||
file="$(get_systemd_service_file docker.socket)"
|
||||
if [ -e "$file" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep "$file" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_11"
|
||||
else
|
||||
warn "$check_1_11"
|
||||
fi
|
||||
else
|
||||
warn "1.11 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
else
|
||||
info "$check_1_11"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
check_1_1_4() {
|
||||
local id="1.1.4"
|
||||
local desc="Ensure auditing is configured for Docker files and directories -/run/containerd (Automated)"
|
||||
local remediation="Install auditd. Add -a exit,always -F path=/run/containerd -F perm=war -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/run/containerd"
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep "$file" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
# 1.12
|
||||
check_1_12="1.12 - Audit Docker files and directories - /etc/default/docker"
|
||||
file="/etc/default/docker"
|
||||
if [ -f "$file" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep $file >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_12"
|
||||
else
|
||||
warn "$check_1_12"
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
else
|
||||
warn "1.12 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
else
|
||||
info "$check_1_12"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
# 1.13
|
||||
check_1_13="1.13 - Audit Docker files and directories - /etc/docker/daemon.json"
|
||||
file="/etc/docker/daemon.json"
|
||||
if [ -f "$file" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep $file >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_13"
|
||||
else
|
||||
warn "$check_1_13"
|
||||
fi
|
||||
else
|
||||
warn "1.13 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
else
|
||||
info "$check_1_13"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
check_1_1_5() {
|
||||
local id="1.1.5"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /var/lib/docker (Automated)"
|
||||
local remediation="Install auditd. Add -w /var/lib/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
directory="/var/lib/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $directory >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
# 1.14
|
||||
check_1_14="1.14 - Audit Docker files and directories - /usr/bin/docker-containerd"
|
||||
file="/usr/bin/docker-containerd"
|
||||
if [ -f "$file" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep $file >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_14"
|
||||
else
|
||||
warn "$check_1_14"
|
||||
fi
|
||||
if grep -s "$directory" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
else
|
||||
warn "1.14 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * Directory not found"
|
||||
logcheckresult "INFO" "Directory not found"
|
||||
}
|
||||
else
|
||||
info "$check_1_14"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
check_1_1_6() {
|
||||
local id="1.1.6"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /etc/docker (Automated)"
|
||||
local remediation="Install auditd. Add -w /etc/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
directory="/etc/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $directory >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
# 1.15
|
||||
check_1_15="1.15 - Audit Docker files and directories - /usr/bin/docker-runc"
|
||||
file="/usr/bin/docker-runc"
|
||||
if [ -f "$file" ]; then
|
||||
command -v auditctl >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
auditctl -l | grep $file >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_1_15"
|
||||
else
|
||||
warn "$check_1_15"
|
||||
fi
|
||||
if grep -s "$directory" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
else
|
||||
warn "1.15 - Failed to inspect: auditctl command not found."
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * Directory not found"
|
||||
logcheckresult "INFO" "Directory not found"
|
||||
}
|
||||
|
||||
check_1_1_7() {
|
||||
local id="1.1.7"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - docker.service (Automated)"
|
||||
local remediation
|
||||
remediation="Install auditd. Add -w $(get_service_file docker.service) -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="$(get_service_file docker.service)"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep "$file" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_8() {
|
||||
local id="1.1.8"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - containerd.sock (Automated)"
|
||||
local remediation
|
||||
remediation="Install auditd. Add -w $(get_service_file containerd.sock) -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="$(get_service_file containerd.sock)"
|
||||
if [ -e "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep "$file" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
check_1_1_9() {
|
||||
local id="1.1.9"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - docker.socket (Automated)"
|
||||
local remediation
|
||||
remediation="Install auditd. Add -w $(get_service_file docker.socket) -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="$(get_service_file docker.socket)"
|
||||
if [ -e "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep "$file" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_10() {
|
||||
local id="1.1.10"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /etc/default/docker (Automated)"
|
||||
local remediation="Install auditd. Add -w /etc/default/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/default/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_11() {
|
||||
local id="1.1.11"
|
||||
local desc="Ensure auditing is configured for Dockerfiles and directories - /etc/docker/daemon.json (Automated)"
|
||||
local remediation="Install auditd. Add -w /etc/docker/daemon.json -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/docker/daemon.json"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_12() {
|
||||
local id="1.1.12"
|
||||
local desc="1.1.12 Ensure auditing is configured for Dockerfiles and directories - /etc/containerd/config.toml (Automated)"
|
||||
local remediation="Install auditd. Add -w /etc/containerd/config.toml -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/containerd/config.toml"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_13() {
|
||||
local id="1.1.13"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /etc/sysconfig/docker (Automated)"
|
||||
local remediation="Install auditd. Add -w /etc/sysconfig/docker -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/sysconfig/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_14() {
|
||||
local id="1.1.14"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /usr/bin/containerd (Automated)"
|
||||
local remediation="Install auditd. Add -w /usr/bin/containerd -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/usr/bin/containerd"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_15() {
|
||||
local id="1.1.15"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /usr/bin/containerd-shim (Automated)"
|
||||
local remediation="Install auditd. Add -w /usr/bin/containerd-shim -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/usr/bin/containerd-shim"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_16() {
|
||||
local id="1.1.16"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /usr/bin/containerd-shim-runc-v1 (Automated)"
|
||||
local remediation="Install auditd. Add -w /usr/bin/containerd-shim-runc-v1 -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/usr/bin/containerd-shim-runc-v1"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_17() {
|
||||
local id="1.1.17"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /usr/bin/containerd-shim-runc-v2 (Automated)"
|
||||
local remediation="Install auditd. Add -w /usr/bin/containerd-shim-runc-v2 -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/usr/bin/containerd-shim-runc-v2"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_1_18() {
|
||||
local id="1.1.18"
|
||||
local desc="Ensure auditing is configured for Docker files and directories - /usr/bin/runc (Automated)"
|
||||
local remediation="Install auditd. Add -w /usr/bin/runc -k docker to the /etc/audit/rules.d/audit.rules file. Then restart the audit daemon using command service auditd restart."
|
||||
local remediationImpact="Audit can generate large log files. So you need to make sure that they are rotated and archived periodically. Create a separate partition for audit logs to avoid filling up other critical partitions."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/usr/bin/runc"
|
||||
if [ -f "$file" ]; then
|
||||
if command -v auditctl >/dev/null 2>&1; then
|
||||
if auditctl -l | grep $file >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if grep -s "$file" "$auditrules" | grep "^[^#;]" 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_1_2() {
|
||||
local id="1.2"
|
||||
local desc="General Configuration"
|
||||
local check="$id - $desc"
|
||||
info "$check"
|
||||
}
|
||||
|
||||
check_1_2_1() {
|
||||
local id="1.2.1"
|
||||
local desc="Ensure the container host has been Hardened (Manual)"
|
||||
local remediation="You may consider various Security Benchmarks for your container host."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_1_2_2() {
|
||||
local id="1.2.2"
|
||||
local desc="Ensure that the version of Docker is up to date (Manual)"
|
||||
local remediation="You should monitor versions of Docker releases and make sure your software is updated as required."
|
||||
local remediationImpact="You should perform a risk assessment regarding Docker version updates and review how they may impact your operations."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
docker_version=$(docker version | grep -i -A2 '^server' | grep ' Version:' \
|
||||
| awk '{print $NF; exit}' | tr -d '[:alpha:]-,')
|
||||
docker_current_version="$(date +%y.%m.0 -d @$(( $(date +%s) - 2592000)))"
|
||||
do_version_check "$docker_current_version" "$docker_version"
|
||||
if [ $? -eq 11 ]; then
|
||||
pass -c "$check"
|
||||
info " * Using $docker_version, verify is it up to date as deemed necessary"
|
||||
logcheckresult "INFO" "Using $docker_version"
|
||||
return
|
||||
fi
|
||||
pass -c "$check"
|
||||
info " * Using $docker_version which is current"
|
||||
info " * Check with your operating system vendor for support and security maintenance for Docker"
|
||||
logcheckresult "PASS" "Using $docker_version"
|
||||
}
|
||||
|
||||
check_1_end() {
|
||||
endsectionjson
|
||||
}
|
||||
else
|
||||
info "$check_1_15"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
|
|
|||
|
|
@ -1,424 +1,196 @@
|
|||
#!/bin/bash
|
||||
#!/bin/sh
|
||||
|
||||
check_2() {
|
||||
logit ""
|
||||
local id="2"
|
||||
local desc="Docker daemon configuration"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
logit "\n"
|
||||
info "2 - Docker Daemon Configuration"
|
||||
|
||||
check_2_1() {
|
||||
local id="2.1"
|
||||
local desc="Run the Docker daemon as a non-root user, if possible (Manual)"
|
||||
local remediation="Follow the current Dockerdocumentation on how to install the Docker daemon as a non-root user."
|
||||
local remediationImpact="There are multiple prerequisites depending on which distribution that is in use, and also known limitations regarding networking and resource limitation. Running in rootless mode also changes the location of any configuration files in use, including all containers using the daemon."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 2.1
|
||||
check_2_1="2.1 - Restrict network traffic between containers"
|
||||
get_docker_effective_command_line_args '--icc' | grep "false" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_1"
|
||||
else
|
||||
warn "$check_2_1"
|
||||
fi
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_2_2() {
|
||||
local id="2.2"
|
||||
local desc="Ensure network traffic is restricted between containers on the default bridge (Scored)"
|
||||
local remediation="Edit the Docker daemon configuration file to ensure that inter-container communication is disabled: icc: false."
|
||||
local remediationImpact="Inter-container communication is disabled on the default network bridge. If any communication between containers on the same host is desired, it needs to be explicitly defined using container linking or custom networks."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if get_docker_effective_command_line_args '--icc' | grep false >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
# 2.2
|
||||
check_2_2="2.2 - Set the logging level"
|
||||
get_docker_effective_command_line_args '-l' >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
get_docker_effective_command_line_args '-l' | grep "info" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_2"
|
||||
else
|
||||
warn "$check_2_2"
|
||||
fi
|
||||
if [[ $(get_docker_configuration_file_args 'icc' | grep "false") ]] && [[ $(get_docker_configuration_file_args 'icc' | grep "false") != "null" ]] ; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
else
|
||||
pass "$check_2_2"
|
||||
fi
|
||||
|
||||
check_2_3() {
|
||||
local id="2.3"
|
||||
local desc="Ensure the logging level is set to 'info' (Scored)"
|
||||
local remediation="Ensure that the Docker daemon configuration file has the following configuration included log-level: info. Alternatively, run the Docker daemon as following: dockerd --log-level=info"
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 2.3
|
||||
check_2_3="2.3 - Allow Docker to make changes to iptables"
|
||||
get_docker_effective_command_line_args '--iptables' | grep "false" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
warn "$check_2_3"
|
||||
else
|
||||
pass "$check_2_3"
|
||||
fi
|
||||
|
||||
if get_docker_configuration_file_args 'log-level' >/dev/null 2>&1; then
|
||||
if get_docker_configuration_file_args 'log-level' | grep info >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if [ -z "$(get_docker_configuration_file_args 'log-level')" ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '-l'; then
|
||||
if get_docker_effective_command_line_args '-l' | grep "info" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
# 2.4
|
||||
check_2_4="2.4 - Do not use insecure registries"
|
||||
get_docker_effective_command_line_args '--insecure-registry' | grep "insecure-registry" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
warn "$check_2_4"
|
||||
else
|
||||
pass "$check_2_4"
|
||||
fi
|
||||
|
||||
check_2_4() {
|
||||
local id="2.4"
|
||||
local desc="Ensure Docker is allowed to make changes to iptables (Scored)"
|
||||
local remediation="Do not run the Docker daemon with --iptables=false option."
|
||||
local remediationImpact="The Docker daemon service requires iptables rules to be enabled before it starts."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 2.5
|
||||
check_2_5="2.5 - Do not use the aufs storage driver"
|
||||
docker info 2>/dev/null | grep -e "^Storage Driver:\s*aufs\s*$" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
warn "$check_2_5"
|
||||
else
|
||||
pass "$check_2_5"
|
||||
fi
|
||||
|
||||
if get_docker_effective_command_line_args '--iptables' | grep "false" >/dev/null 2>&1; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if [[ $(get_docker_configuration_file_args 'iptables' | grep "false") ]] && [[ $(get_docker_configuration_file_args 'iptables' | grep "false") != "null" ]] ; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_2_5() {
|
||||
local id="2.5"
|
||||
local desc="Ensure insecure registries are not used (Scored)"
|
||||
local remediation="You should ensure that no insecure registries are in use."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if get_docker_effective_command_line_args '--insecure-registry' | grep "insecure-registry" >/dev/null 2>&1; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if [[ $(get_docker_configuration_file_args 'insecure-registries' | grep -v '\[]') ]] && [[ $(get_docker_configuration_file_args 'insecure-registries' | grep -v '\[]') != "null" ]] ; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_2_6() {
|
||||
local id="2.6"
|
||||
local desc="Ensure aufs storage driver is not used (Scored)"
|
||||
local remediation="Do not start Docker daemon as using dockerd --storage-driver aufs option."
|
||||
local remediationImpact="aufs is the only storage driver that allows containers to share executable and shared library memory. Its use should be reviewed in line with your organization's security policy."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "^\sStorage Driver:\s*aufs\s*$" >/dev/null 2>&1; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_2_7() {
|
||||
local id="2.7"
|
||||
local desc="Ensure TLS authentication for Docker daemon is configured (Scored)"
|
||||
local remediation="Follow the steps mentioned in the Docker documentation or other references. By default, TLS authentication is not configured."
|
||||
local remediationImpact="You would need to manage and guard certificates and keys for the Docker daemon and Docker clients."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if $(grep -qE "host.*tcp://" "$CONFIG_FILE") || \
|
||||
[ $(get_docker_cumulative_command_line_args '-H' | grep -vE '(unix|fd)://') > /dev/null 2>&1 ]; then
|
||||
if [ $(get_docker_configuration_file_args '"tlsverify":' | grep 'true') ] || \
|
||||
[ $(get_docker_cumulative_command_line_args '--tlsverify' | grep 'tlsverify') >/dev/null 2>&1 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if [ $(get_docker_configuration_file_args '"tls":' | grep 'true') ] || \
|
||||
[ $(get_docker_cumulative_command_line_args '--tls' | grep 'tls$') >/dev/null 2>&1 ]; then
|
||||
warn -s "$check"
|
||||
# 2.6
|
||||
check_2_6="2.6 - Configure TLS authentication for Docker daemon"
|
||||
get_docker_cumulative_command_line_args '-H' | grep -vE '(unix|fd)://' >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
get_docker_cumulative_command_line_args '--tlskey' | grep 'tlskey=' >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
get_docker_cumulative_command_line_args '--tlsverify' | grep 'tlsverify' >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_6"
|
||||
#pass " * Docker daemon currently listening on TCP with TLS and verification"
|
||||
else
|
||||
warn "$check_2_6"
|
||||
warn " * Docker daemon currently listening on TCP with TLS, but no verification"
|
||||
logcheckresult "WARN" "Docker daemon currently listening on TCP with TLS, but no verification"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
else
|
||||
warn "$check_2_6"
|
||||
warn " * Docker daemon currently listening on TCP without TLS"
|
||||
logcheckresult "WARN" "Docker daemon currently listening on TCP without TLS"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_2_6"
|
||||
info " * Docker daemon not listening on TCP"
|
||||
logcheckresult "INFO" "Docker daemon not listening on TCP"
|
||||
}
|
||||
fi
|
||||
|
||||
check_2_8() {
|
||||
local id="2.8"
|
||||
local desc="Ensure the default ulimit is configured appropriately (Manual)"
|
||||
local remediation="Run Docker in daemon mode and pass --default-ulimit as option with respective ulimits as appropriate in your environment and in line with your security policy. Example: dockerd --default-ulimit nproc=1024:2048 --default-ulimit nofile=100:200"
|
||||
local remediationImpact="If ulimits are set incorrectly this could cause issues with system resources, possibly causing a denial of service condition."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if [[ $(get_docker_configuration_file_args 'default-ulimits' | grep -v '{}') ]] && [[ $(get_docker_configuration_file_args 'default-ulimits' | grep -v '{}') != "null" ]] ; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--default-ulimit' | grep "default-ulimit" >/dev/null 2>&1; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
# 2.7
|
||||
check_2_7="2.7 - Set default ulimit as appropriate"
|
||||
get_docker_effective_command_line_args '--default-ulimit' | grep "default-ulimit" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_7"
|
||||
else
|
||||
info "$check_2_7"
|
||||
info " * Default ulimit doesn't appear to be set"
|
||||
logcheckresult "INFO" "Default ulimit doesn't appear to be set"
|
||||
}
|
||||
fi
|
||||
|
||||
check_2_9() {
|
||||
local id="2.9"
|
||||
local desc="Enable user namespace support (Scored)"
|
||||
local remediation="Please consult the Docker documentation for various ways in which this can be configured depending upon your requirements. The high-level steps are: Ensure that the files /etc/subuid and /etc/subgid exist. Start the docker daemon with --userns-remap flag."
|
||||
local remediationImpact="User namespace remapping is incompatible with a number of Docker features and also currently breaks some of its functionalities."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 2.8
|
||||
check_2_8="2.8 - Enable user namespace support"
|
||||
get_docker_effective_command_line_args '--userns-remap' | grep "userns-remap" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_8"
|
||||
else
|
||||
warn "$check_2_8"
|
||||
fi
|
||||
|
||||
if [[ $(get_docker_configuration_file_args 'userns-remap' | grep -v '""') ]] && [[ $(get_docker_configuration_file_args 'userns-remap' | grep -v '""') != "null" ]] ; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
# 2.9
|
||||
check_2_9="2.9 - Confirm default cgroup usage"
|
||||
get_docker_effective_command_line_args '--cgroup-parent' | grep "cgroup-parent" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
info "$check_2_9"
|
||||
info " * Confirm cgroup usage"
|
||||
else
|
||||
pass "$check_2_9"
|
||||
fi
|
||||
|
||||
# 2.10
|
||||
check_2_10="2.10 - Do not change base device size until needed"
|
||||
get_docker_effective_command_line_args '--storage-opt' | grep "dm.basesize" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
warn "$check_2_10"
|
||||
else
|
||||
pass "$check_2_10"
|
||||
fi
|
||||
|
||||
# 2.11
|
||||
check_2_11="2.11 - Use authorization plugin"
|
||||
get_docker_effective_command_line_args '--authorization-plugin' | grep "authorization-plugin" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_11"
|
||||
else
|
||||
warn "$check_2_11"
|
||||
fi
|
||||
|
||||
# 2.12
|
||||
check_2_12="2.12 - Configure centralized and remote logging"
|
||||
get_docker_effective_command_line_args '--log-driver' | grep "log-driver" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_12"
|
||||
else
|
||||
warn "$check_2_12"
|
||||
fi
|
||||
|
||||
# 2.13
|
||||
check_2_13="2.13 - Disable operations on legacy registry (v1)"
|
||||
get_docker_effective_command_line_args '--disable-legacy-registry' | grep "disable-legacy-registry" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_13"
|
||||
else
|
||||
warn "$check_2_13"
|
||||
fi
|
||||
|
||||
# 2.14
|
||||
check_2_14="2.14 - Enable live restore"
|
||||
get_docker_effective_command_line_args '--live-restore' 2>/dev/null | grep "live-restore" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_14"
|
||||
else
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
pass "$check_2_14 (Incompatible with swarm mode)"
|
||||
else
|
||||
warn "$check_2_14"
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--userns-remap' | grep "userns-remap" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
|
||||
# 2.15
|
||||
check_2_15="2.15 - Do not enable swarm mode, if not needed"
|
||||
docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1
|
||||
if [ $? -eq 1 ]; then
|
||||
pass "$check_2_15"
|
||||
else
|
||||
warn "$check_2_15"
|
||||
fi
|
||||
|
||||
# 2.16
|
||||
check_2_16="2.16 - Control the number of manager nodes in a swarm"
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
managernodes=$(docker node ls | grep "Leader" | wc -l)
|
||||
if [ $managernodes -le 1 ]; then
|
||||
pass "$check_2_16"
|
||||
else
|
||||
warn "$check_2_16"
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
else
|
||||
pass "$check_2_16 (Swarm mode not enabled)"
|
||||
fi
|
||||
|
||||
check_2_10() {
|
||||
local id="2.10"
|
||||
local desc="Ensure the default cgroup usage has been confirmed (Scored)"
|
||||
local remediation="The default setting is in line with good security practice and can be left in situ."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 2.17
|
||||
check_2_17="2.17 - Bind swarm services to a specific host interface"
|
||||
netstat -lt | grep -e '\[::]:2377' -e '*:2377' -e '0.0.0.0:2377' >/dev/null 2>&1
|
||||
if [ $? -eq 1 ]; then
|
||||
pass "$check_2_17"
|
||||
else
|
||||
warn "$check_2_17"
|
||||
fi
|
||||
|
||||
if get_docker_configuration_file_args 'cgroup-parent' | grep -v ''; then
|
||||
warn -s "$check"
|
||||
info " * Confirm cgroup usage"
|
||||
logcheckresult "WARN" "Confirm cgroup usage"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--cgroup-parent' | grep "cgroup-parent" >/dev/null 2>&1; then
|
||||
warn -s "$check"
|
||||
info " * Confirm cgroup usage"
|
||||
logcheckresult "WARN" "Confirm cgroup usage"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_2_11() {
|
||||
local id="2.11"
|
||||
local desc="Ensure base device size is not changed until needed (Scored)"
|
||||
local remediation="Do not set --storage-opt dm.basesize until needed."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if get_docker_configuration_file_args 'storage-opts' | grep "dm.basesize" >/dev/null 2>&1; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--storage-opt' | grep "dm.basesize" >/dev/null 2>&1; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_2_12() {
|
||||
local id="2.12"
|
||||
local desc="Ensure that authorization for Docker client commands is enabled (Scored)"
|
||||
local remediation="Install/Create an authorization plugin. Configure the authorization policy as desired. Start the docker daemon using command dockerd --authorization-plugin=<PLUGIN_ID>"
|
||||
local remediationImpact="Each Docker command needs to pass through the authorization plugin mechanism. This may have a performance impact"
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if [[ $(get_docker_configuration_file_args 'authorization-plugins' | grep -v '\[]') ]] && [[ $(get_docker_configuration_file_args 'authorization-plugins' | grep -v '\[]') != "null" ]] ; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--authorization-plugin' | grep "authorization-plugin" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
|
||||
check_2_13() {
|
||||
local id="2.13"
|
||||
local desc="Ensure centralized and remote logging is configured (Scored)"
|
||||
local remediation="Set up the desired log driver following its documentation. Start the docker daemon using that logging driver. Example: dockerd --log-driver=syslog --log-opt syslog-address=tcp://192.xxx.xxx.xxx"
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info --format '{{ .LoggingDriver }}' | grep 'json-file' >/dev/null 2>&1; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_2_14() {
|
||||
local id="2.14"
|
||||
local desc="Ensure containers are restricted from acquiring new privileges (Scored)"
|
||||
local remediation="You should run the Docker daemon using command: dockerd --no-new-privileges"
|
||||
local remediationImpact="no_new_priv prevents LSMs such as SELinux from escalating the privileges of individual containers."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if get_docker_effective_command_line_args '--no-new-privileges' | grep "no-new-privileges" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if get_docker_configuration_file_args 'no-new-privileges' | grep true >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
|
||||
check_2_15() {
|
||||
local id="2.15"
|
||||
local desc="Ensure live restore is enabled (Scored)"
|
||||
local remediation="Run Docker in daemon mode and pass --live-restore option."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Live Restore Enabled:\s*true\s*" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if docker info 2>/dev/null | grep -e "Swarm:*\sactive\s*" >/dev/null 2>&1; then
|
||||
pass -s "$check (Incompatible with swarm mode)"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--live-restore' | grep "live-restore" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
|
||||
check_2_16() {
|
||||
local id="2.16"
|
||||
local desc="Ensure Userland Proxy is Disabled (Scored)"
|
||||
local remediation="You should run the Docker daemon using command: dockerd --userland-proxy=false"
|
||||
local remediationImpact="Some systems with older Linux kernels may not be able to support hairpin NAT and therefore require the userland proxy service. Also, some networking setups can be impacted by the removal of the userland proxy."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if get_docker_configuration_file_args 'userland-proxy' | grep false >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--userland-proxy=false' 2>/dev/null | grep "userland-proxy=false" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
|
||||
check_2_17() {
|
||||
local id="2.17"
|
||||
local desc="Ensure that a daemon-wide custom seccomp profile is applied if appropriate (Manual)"
|
||||
local remediation="By default, Docker's default seccomp profile is applied. If this is adequate for your environment, no action is necessary."
|
||||
local remediationImpact="A misconfigured seccomp profile could possibly interrupt your container environment. You should therefore exercise extreme care if you choose to override the default settings."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info --format '{{ .SecurityOptions }}' | grep 'name=seccomp,profile=default' 2>/dev/null 1>&2; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_2_18() {
|
||||
docker_version=$(docker version | grep -i -A2 '^server' | grep ' Version:' \
|
||||
| awk '{print $NF; exit}' | tr -d '[:alpha:]-,.' | cut -c 1-4)
|
||||
|
||||
local id="2.18"
|
||||
local desc="Ensure that experimental features are not implemented in production (Scored)"
|
||||
local remediation="You should not pass --experimental as a runtime parameter to the Docker daemon on production systems."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if [ "$docker_version" -le 1903 ]; then
|
||||
if docker version -f '{{.Server.Experimental}}' | grep false 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
local desc="$desc (Deprecated)"
|
||||
local check="$id - $desc"
|
||||
info -c "$desc"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_2_end() {
|
||||
endsectionjson
|
||||
}
|
||||
# 2.18
|
||||
check_2_18="2.18 - Disable Userland Proxy"
|
||||
get_docker_effective_command_line_args '--userland-proxy=false' 2>/dev/null | grep "userland-proxy=false" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
pass "$check_2_18"
|
||||
else
|
||||
warn "$check_2_18"
|
||||
fi
|
||||
|
|
|
|||
|
|
@ -1,646 +1,324 @@
|
|||
#!/bin/bash
|
||||
#!/bin/sh
|
||||
|
||||
check_3() {
|
||||
logit ""
|
||||
local id="3"
|
||||
local desc="Docker daemon configuration files"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
logit "\n"
|
||||
info "3 - Docker Daemon Configuration Files"
|
||||
|
||||
check_3_1() {
|
||||
local id="3.1"
|
||||
local desc="Ensure that the docker.service file ownership is set to root:root (Automated)"
|
||||
local remediation="Find out the file location: systemctl show -p FragmentPath docker.service. If the file does not exist, this recommendation is not applicable. If the file does exist, you should run the command chown root:root <path>, in order to set the ownership and group ownership for the file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file=$(get_service_file docker.service)
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %u%g "$file")" -eq 00 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
# 3.1
|
||||
check_3_1="3.1 - Verify that docker.service file ownership is set to root:root"
|
||||
file="$(get_systemd_service_file docker.service)"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %u%g $file)" -eq 00 ]; then
|
||||
pass "$check_3_1"
|
||||
else
|
||||
warn "$check_3_1"
|
||||
warn " * Wrong ownership for $file"
|
||||
logcheckresult "WARN" "Wrong ownership for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_1"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_2() {
|
||||
local id="3.2"
|
||||
local desc="Ensure that docker.service file permissions are appropriately set (Automated)"
|
||||
local remediation="Find out the file location: systemctl show -p FragmentPath docker.service. If the file does not exist, this recommendation is not applicable. If the file exists, run the command chmod 644 <path> to set the file permissions to 644."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file=$(get_service_file docker.service)
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a "$file")" -le 644 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
# 3.2
|
||||
check_3_2="3.2 - Verify that docker.service file permissions are set to 644 or more restrictive"
|
||||
file="$(get_systemd_service_file docker.service)"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -eq 644 -o "$(stat -c %a $file)" -eq 600 ]; then
|
||||
pass "$check_3_2"
|
||||
else
|
||||
warn "$check_3_2"
|
||||
warn " * Wrong permissions for $file"
|
||||
logcheckresult "WARN" "Wrong permissions for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_2"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_3() {
|
||||
local id="3.3"
|
||||
local desc="Ensure that docker.socket file ownership is set to root:root (Automated)"
|
||||
local remediation="Find out the file location: systemctl show -p FragmentPath docker.socket. If the file does not exist, this recommendation is not applicable. If the file exists, run the command chown root:root <path> to set the ownership and group ownership for the file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file=$(get_service_file docker.socket)
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %u%g "$file")" -eq 00 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
# 3.3
|
||||
check_3_3="3.3 - Verify that docker.socket file ownership is set to root:root"
|
||||
file="$(get_systemd_service_file docker.socket)"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %u%g $file)" -eq 00 ]; then
|
||||
pass "$check_3_3"
|
||||
else
|
||||
warn "$check_3_3"
|
||||
warn " * Wrong ownership for $file"
|
||||
logcheckresult "WARN" "Wrong ownership for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_3"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_4() {
|
||||
local id="3.4"
|
||||
local desc="Ensure that docker.socket file permissions are set to 644 or more restrictive (Automated)"
|
||||
local remediation="Find out the file location: systemctl show -p FragmentPath docker.socket. If the file does not exist, this recommendation is not applicable. If the file does exist, you should run the command chmod 644 <path> to set the file permissions to 644."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file=$(get_service_file docker.socket)
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a "$file")" -le 644 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
# 3.4
|
||||
check_3_4="3.4 - Verify that docker.socket file permissions are set to 644 or more restrictive"
|
||||
file="$(get_systemd_service_file docker.socket)"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -eq 644 -o "$(stat -c %a $file)" -eq 600 ]; then
|
||||
pass "$check_3_4"
|
||||
else
|
||||
warn "$check_3_4"
|
||||
warn " * Wrong permissions for $file"
|
||||
logcheckresult "WARN" "Wrong permissions for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_4"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_5() {
|
||||
local id="3.5"
|
||||
local desc="Ensure that the /etc/docker directory ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root /etc/docker. This sets the ownership and group ownership for the directory to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
directory="/etc/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
if [ "$(stat -c %u%g $directory)" -eq 00 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
# 3.5
|
||||
check_3_5="3.5 - Verify that /etc/docker directory ownership is set to root:root"
|
||||
directory="/etc/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
if [ "$(stat -c %u%g $directory)" -eq 00 ]; then
|
||||
pass "$check_3_5"
|
||||
else
|
||||
warn "$check_3_5"
|
||||
warn " * Wrong ownership for $directory"
|
||||
logcheckresult "WARN" "Wrong ownership for $directory"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_5"
|
||||
info " * Directory not found"
|
||||
logcheckresult "INFO" "Directory not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_6() {
|
||||
local id="3.6"
|
||||
local desc="Ensure that /etc/docker directory permissions are set to 755 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 755 /etc/docker. This sets the permissions for the directory to 755."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
directory="/etc/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
if [ "$(stat -c %a $directory)" -le 755 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
# 3.6
|
||||
check_3_6="3.6 - Verify that /etc/docker directory permissions are set to 755 or more restrictive"
|
||||
directory="/etc/docker"
|
||||
if [ -d "$directory" ]; then
|
||||
if [ "$(stat -c %a $directory)" -eq 755 ]; then
|
||||
pass "$check_3_6"
|
||||
elif [ "$(stat -c %a $directory)" -eq 700 ]; then
|
||||
pass "$check_3_6"
|
||||
else
|
||||
warn "$check_3_6"
|
||||
warn " * Wrong permissions for $directory"
|
||||
logcheckresult "WARN" "Wrong permissions for $directory"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_6"
|
||||
info " * Directory not found"
|
||||
logcheckresult "INFO" "Directory not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_7() {
|
||||
local id="3.7"
|
||||
local desc="Ensure that registry certificate file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root /etc/docker/certs.d/<registry-name>/*. This would set the individual ownership and group ownership for the registry certificate files to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
directory="/etc/docker/certs.d/"
|
||||
if [ -d "$directory" ]; then
|
||||
fail=0
|
||||
owners=$(find "$directory" -type f -name '*.crt')
|
||||
for p in $owners; do
|
||||
if [ "$(stat -c %u "$p")" -ne 0 ]; then
|
||||
fail=1
|
||||
fi
|
||||
done
|
||||
if [ $fail -eq 1 ]; then
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $directory"
|
||||
logcheckresult "WARN" "Wrong ownership for $directory"
|
||||
return
|
||||
# 3.7
|
||||
check_3_7="3.7 - Verify that registry certificate file ownership is set to root:root"
|
||||
directory="/etc/docker/certs.d/"
|
||||
if [ -d "$directory" ]; then
|
||||
fail=0
|
||||
owners=$(ls -lL $directory | grep ".crt" | awk '{print $3, $4}')
|
||||
for p in $owners; do
|
||||
printf "%s" "$p" | grep "root" >/dev/null 2>&1
|
||||
if [ $? -ne 0 ]; then
|
||||
fail=1
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
done
|
||||
if [ $fail -eq 1 ]; then
|
||||
warn "$check_3_7"
|
||||
warn " * Wrong ownership for $directory"
|
||||
else
|
||||
pass "$check_3_7"
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_7"
|
||||
info " * Directory not found"
|
||||
logcheckresult "INFO" "Directory not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_8() {
|
||||
local id="3.8"
|
||||
local desc="Ensure that registry certificate file permissions are set to 444 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 444 /etc/docker/certs.d/<registry-name>/*. This would set the permissions for the registry certificate files to 444."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
directory="/etc/docker/certs.d/"
|
||||
if [ -d "$directory" ]; then
|
||||
fail=0
|
||||
perms=$(find "$directory" -type f -name '*.crt')
|
||||
for p in $perms; do
|
||||
if [ "$(stat -c %a "$p")" -gt 444 ]; then
|
||||
fail=1
|
||||
fi
|
||||
done
|
||||
if [ $fail -eq 1 ]; then
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $directory"
|
||||
logcheckresult "WARN" "Wrong permissions for $directory"
|
||||
return
|
||||
# 3.8
|
||||
check_3_8="3.8 - Verify that registry certificate file permissions are set to 444 or more restrictive"
|
||||
directory="/etc/docker/certs.d/"
|
||||
if [ -d "$directory" ]; then
|
||||
fail=0
|
||||
perms=$(ls -lL $directory | grep ".crt" | awk '{print $1}')
|
||||
for p in $perms; do
|
||||
if [ "$p" != "-r--r--r--." -a "$p" = "-r--------." ]; then
|
||||
fail=1
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
done
|
||||
if [ $fail -eq 1 ]; then
|
||||
warn "$check_3_8"
|
||||
warn " * Wrong permissions for $directory"
|
||||
else
|
||||
pass "$check_3_8"
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_8"
|
||||
info " * Directory not found"
|
||||
logcheckresult "INFO" "Directory not found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_9() {
|
||||
local id="3.9"
|
||||
local desc="Ensure that TLS CA certificate file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root <path to TLS CA certificate file>. This sets the individual ownership and group ownership for the TLS CA certificate file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
tlscacert=$(get_docker_effective_command_line_args '--tlscacert' | sed -n 's/.*tlscacert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -n "$(get_docker_configuration_file_args 'tlscacert')" ]; then
|
||||
tlscacert=$(get_docker_configuration_file_args 'tlscacert')
|
||||
fi
|
||||
if [ -f "$tlscacert" ]; then
|
||||
if [ "$(stat -c %u%g "$tlscacert")" -eq 00 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
# 3.9
|
||||
check_3_9="3.9 - Verify that TLS CA certificate file ownership is set to root:root"
|
||||
tlscacert=$(get_docker_effective_command_line_args '--tlscacert' | sed -n 's/.*tlscacert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -f "$tlscacert" ]; then
|
||||
if [ "$(stat -c %u%g "$tlscacert")" -eq 00 ]; then
|
||||
pass "$check_3_9"
|
||||
else
|
||||
warn "$check_3_9"
|
||||
warn " * Wrong ownership for $tlscacert"
|
||||
logcheckresult "WARN" "Wrong ownership for $tlscacert"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
else
|
||||
info "$check_3_9"
|
||||
info " * No TLS CA certificate found"
|
||||
logcheckresult "INFO" "No TLS CA certificate found"
|
||||
}
|
||||
fi
|
||||
|
||||
check_3_10() {
|
||||
local id="3.10"
|
||||
local desc="Ensure that TLS CA certificate file permissions are set to 444 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 444 <path to TLS CA certificate file>. This sets the file permissions on the TLS CA file to 444."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
tlscacert=$(get_docker_effective_command_line_args '--tlscacert' | sed -n 's/.*tlscacert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -n "$(get_docker_configuration_file_args 'tlscacert')" ]; then
|
||||
tlscacert=$(get_docker_configuration_file_args 'tlscacert')
|
||||
# 3.10
|
||||
check_3_10="3.10 - Verify that TLS CA certificate file permissions are set to 444 or more restrictive"
|
||||
tlscacert=$(get_docker_effective_command_line_args '--tlscacert' | sed -n 's/.*tlscacert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -f "$tlscacert" ]; then
|
||||
perms=$(ls -ld "$tlscacert" | awk '{print $1}')
|
||||
if [ "$perms" = "-r--r--r--" ]; then
|
||||
pass "$check_3_10"
|
||||
else
|
||||
warn "$check_3_10"
|
||||
warn " * Wrong permissions for $tlscacert"
|
||||
fi
|
||||
if [ -f "$tlscacert" ]; then
|
||||
if [ "$(stat -c %a "$tlscacert")" -le 444 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $tlscacert"
|
||||
logcheckresult "WARN" "Wrong permissions for $tlscacert"
|
||||
return
|
||||
else
|
||||
info "$check_3_10"
|
||||
info " * No TLS CA certificate found"
|
||||
fi
|
||||
|
||||
# 3.11
|
||||
check_3_11="3.11 - Verify that Docker server certificate file ownership is set to root:root"
|
||||
tlscert=$(get_docker_effective_command_line_args '--tlscert' | sed -n 's/.*tlscert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -f "$tlscert" ]; then
|
||||
if [ "$(stat -c %u%g "$tlscert")" -eq 00 ]; then
|
||||
pass "$check_3_11"
|
||||
else
|
||||
warn "$check_3_11"
|
||||
warn " * Wrong ownership for $tlscert"
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * No TLS CA certificate found"
|
||||
logcheckresult "INFO" "No TLS CA certificate found"
|
||||
}
|
||||
else
|
||||
info "$check_3_11"
|
||||
info " * No TLS Server certificate found"
|
||||
fi
|
||||
|
||||
check_3_11() {
|
||||
local id="3.11"
|
||||
local desc="Ensure that Docker server certificate file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root <path to Docker server certificate file>. This sets the individual ownership and the group ownership for the Docker server certificate file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
tlscert=$(get_docker_effective_command_line_args '--tlscert' | sed -n 's/.*tlscert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -n "$(get_docker_configuration_file_args 'tlscert')" ]; then
|
||||
tlscert=$(get_docker_configuration_file_args 'tlscert')
|
||||
# 3.12
|
||||
check_3_12="3.12 - Verify that Docker server certificate file permissions are set to 444 or more restrictive"
|
||||
tlscert=$(get_docker_effective_command_line_args '--tlscert' | sed -n 's/.*tlscert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -f "$tlscert" ]; then
|
||||
perms=$(ls -ld "$tlscert" | awk '{print $1}')
|
||||
if [ "$perms" = "-r--r--r--" ]; then
|
||||
pass "$check_3_12"
|
||||
else
|
||||
warn "$check_3_12"
|
||||
warn " * Wrong permissions for $tlscert"
|
||||
fi
|
||||
if [ -f "$tlscert" ]; then
|
||||
if [ "$(stat -c %u%g "$tlscert")" -eq 00 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $tlscert"
|
||||
logcheckresult "WARN" "Wrong ownership for $tlscert"
|
||||
return
|
||||
else
|
||||
info "$check_3_12"
|
||||
info " * No TLS Server certificate found"
|
||||
fi
|
||||
|
||||
# 3.13
|
||||
check_3_13="3.13 - Verify that Docker server key file ownership is set to root:root"
|
||||
tlskey=$(get_docker_effective_command_line_args '--tlskey' | sed -n 's/.*tlskey=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -f "$tlskey" ]; then
|
||||
if [ "$(stat -c %u%g "$tlskey")" -eq 00 ]; then
|
||||
pass "$check_3_13"
|
||||
else
|
||||
warn "$check_3_13"
|
||||
warn " * Wrong ownership for $tlskey"
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * No TLS Server certificate found"
|
||||
logcheckresult "INFO" "No TLS Server certificate found"
|
||||
}
|
||||
else
|
||||
info "$check_3_13"
|
||||
info " * No TLS Key found"
|
||||
fi
|
||||
|
||||
check_3_12() {
|
||||
local id="3.12"
|
||||
local desc="Ensure that the Docker server certificate file permissions are set to 444 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 444 <path to Docker server certificate file>. This sets the file permissions of the Docker server certificate file to 444."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
tlscert=$(get_docker_effective_command_line_args '--tlscert' | sed -n 's/.*tlscert=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -n "$(get_docker_configuration_file_args 'tlscert')" ]; then
|
||||
tlscert=$(get_docker_configuration_file_args 'tlscert')
|
||||
# 3.14
|
||||
check_3_14="3.14 - Verify that Docker server key file permissions are set to 400 or more restrictive"
|
||||
tlskey=$(get_docker_effective_command_line_args '--tlskey' | sed -n 's/.*tlskey=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -f "$tlskey" ]; then
|
||||
perms=$(ls -ld "$tlskey" | awk '{print $1}')
|
||||
if [ "$perms" = "-r--------" ]; then
|
||||
pass "$check_3_14"
|
||||
else
|
||||
warn "$check_3_14"
|
||||
warn " * Wrong permissions for $tlskey"
|
||||
fi
|
||||
if [ -f "$tlscert" ]; then
|
||||
if [ "$(stat -c %a "$tlscert")" -le 444 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $tlscert"
|
||||
logcheckresult "WARN" "Wrong permissions for $tlscert"
|
||||
return
|
||||
else
|
||||
info "$check_3_14"
|
||||
info " * No TLS Key found"
|
||||
fi
|
||||
|
||||
# 3.15
|
||||
check_3_15="3.15 - Verify that Docker socket file ownership is set to root:docker"
|
||||
file="/var/run/docker.sock"
|
||||
if [ -S "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:docker' ]; then
|
||||
pass "$check_3_15"
|
||||
else
|
||||
warn "$check_3_15"
|
||||
warn " * Wrong ownership for $file"
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * No TLS Server certificate found"
|
||||
logcheckresult "INFO" "No TLS Server certificate found"
|
||||
}
|
||||
else
|
||||
info "$check_3_15"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
check_3_13() {
|
||||
local id="3.13"
|
||||
local desc="Ensure that the Docker server certificate key file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root <path to Docker server certificate key file>. This sets the individual ownership and group ownership for the Docker server certificate key file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
tlskey=$(get_docker_effective_command_line_args '--tlskey' | sed -n 's/.*tlskey=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -n "$(get_docker_configuration_file_args 'tlskey')" ]; then
|
||||
tlskey=$(get_docker_configuration_file_args 'tlskey')
|
||||
# 3.16
|
||||
check_3_16="3.16 - Verify that Docker socket file permissions are set to 660 or more restrictive"
|
||||
file="/var/run/docker.sock"
|
||||
if [ -S "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -eq 660 -o "$(stat -c %a $file)" -eq 600 ]; then
|
||||
pass "$check_3_16"
|
||||
else
|
||||
warn "$check_3_16"
|
||||
warn " * Wrong permissions for $file"
|
||||
fi
|
||||
if [ -f "$tlskey" ]; then
|
||||
if [ "$(stat -c %u%g "$tlskey")" -eq 00 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $tlskey"
|
||||
logcheckresult "WARN" "Wrong ownership for $tlskey"
|
||||
return
|
||||
else
|
||||
info "$check_3_16"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
# 3.17
|
||||
check_3_17="3.17 - Verify that daemon.json file ownership is set to root:root"
|
||||
file="/etc/docker/daemon.json"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:root' ]; then
|
||||
pass "$check_3_17"
|
||||
else
|
||||
warn "$check_3_17"
|
||||
warn " * Wrong ownership for $file"
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * No TLS Key found"
|
||||
logcheckresult "INFO" "No TLS Key found"
|
||||
}
|
||||
else
|
||||
info "$check_3_17"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
check_3_14() {
|
||||
local id="3.14"
|
||||
local desc="Ensure that the Docker server certificate key file permissions are set to 400 (Automated)"
|
||||
local remediation="You should run the following command: chmod 400 <path to Docker server certificate key file>. This sets the Docker server certificate key file permissions to 400."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
tlskey=$(get_docker_effective_command_line_args '--tlskey' | sed -n 's/.*tlskey=\([^s]\)/\1/p' | sed 's/--/ --/g' | cut -d " " -f 1)
|
||||
if [ -n "$(get_docker_configuration_file_args 'tlskey')" ]; then
|
||||
tlskey=$(get_docker_configuration_file_args 'tlskey')
|
||||
# 3.18
|
||||
check_3_18="3.18 - Verify that daemon.json file permissions are set to 644 or more restrictive"
|
||||
file="/etc/docker/daemon.json"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -eq 644 -o "$(stat -c %a $file)" -eq 600 ]; then
|
||||
pass "$check_3_18"
|
||||
else
|
||||
warn "$check_3_18"
|
||||
warn " * Wrong permissions for $file"
|
||||
fi
|
||||
if [ -f "$tlskey" ]; then
|
||||
if [ "$(stat -c %a "$tlskey")" -eq 400 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $tlskey"
|
||||
logcheckresult "WARN" "Wrong permissions for $tlskey"
|
||||
return
|
||||
else
|
||||
info "$check_3_18"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
# 3.19
|
||||
check_3_19="3.19 - Verify that /etc/default/docker file ownership is set to root:root"
|
||||
file="/etc/default/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:root' ]; then
|
||||
pass "$check_3_19"
|
||||
else
|
||||
warn "$check_3_19"
|
||||
warn " * Wrong ownership for $file"
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * No TLS Key found"
|
||||
logcheckresult "INFO" "No TLS Key found"
|
||||
}
|
||||
else
|
||||
info "$check_3_19"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
||||
check_3_15() {
|
||||
local id="3.15"
|
||||
local desc="Ensure that the Docker socket file ownership is set to root:docker (Automated)"
|
||||
local remediation="You should run the following command: chown root:docker /var/run/docker.sock. This sets the ownership to root and group ownership to docker for the default Docker socket file."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/var/run/docker.sock"
|
||||
if [ -S "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:docker' ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $file"
|
||||
logcheckresult "WARN" "Wrong ownership for $file"
|
||||
return
|
||||
# 3.20
|
||||
check_3_20="3.20 - Verify that /etc/default/docker file permissions are set to 644 or more restrictive"
|
||||
file="/etc/default/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -eq 644 -o "$(stat -c %a $file)" -eq 600 ]; then
|
||||
pass "$check_3_20"
|
||||
else
|
||||
warn "$check_3_20"
|
||||
warn " * Wrong permissions for $file"
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_16() {
|
||||
local id="3.16"
|
||||
local desc="Ensure that the Docker socket file permissions are set to 660 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 660 /var/run/docker.sock. This sets the file permissions of the Docker socket file to 660."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/var/run/docker.sock"
|
||||
if [ -S "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -le 660 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $file"
|
||||
logcheckresult "WARN" "Wrong permissions for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_17() {
|
||||
local id="3.17"
|
||||
local desc="Ensure that the daemon.json file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root /etc/docker/daemon.json. This sets the ownership and group ownership for the file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/docker/daemon.json"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:root' ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $file"
|
||||
logcheckresult "WARN" "Wrong ownership for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_18() {
|
||||
local id="3.18"
|
||||
local desc="Ensure that daemon.json file permissions are set to 644 or more restrictive (Automated)"
|
||||
local remediation="You should run the following command: chmod 644 /etc/docker/daemon.json. This sets the file permissions for this file to 644."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/docker/daemon.json"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -le 644 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $file"
|
||||
logcheckresult "WARN" "Wrong permissions for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_19() {
|
||||
local id="3.19"
|
||||
local desc="Ensure that the /etc/default/docker file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root /etc/default/docker. This sets the ownership and group ownership of the file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/default/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:root' ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $file"
|
||||
logcheckresult "WARN" "Wrong ownership for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_20() {
|
||||
local id="3.20"
|
||||
local desc="Ensure that the /etc/default/docker file permissions are set to 644 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 644 /etc/default/docker. This sets the file permissions for this file to 644."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/default/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -le 644 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $file"
|
||||
logcheckresult "WARN" "Wrong permissions for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_21() {
|
||||
local id="3.21"
|
||||
local desc="Ensure that the /etc/sysconfig/docker file permissions are set to 644 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 644 /etc/sysconfig/docker. This sets the file permissions for this file to 644."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/sysconfig/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -le 644 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $file"
|
||||
logcheckresult "WARN" "Wrong permissions for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_22() {
|
||||
local id="3.22"
|
||||
local desc="Ensure that the /etc/sysconfig/docker file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root /etc/sysconfig/docker. This sets the ownership and group ownership for the file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/etc/sysconfig/docker"
|
||||
if [ -f "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:root' ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $file"
|
||||
logcheckresult "WARN" "Wrong ownership for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_23() {
|
||||
local id="3.23"
|
||||
local desc="Ensure that the Containerd socket file ownership is set to root:root (Automated)"
|
||||
local remediation="You should run the following command: chown root:root /run/containerd/containerd.sock. This sets the ownership and group ownership for the file to root."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/run/containerd/containerd.sock"
|
||||
if [ -S "$file" ]; then
|
||||
if [ "$(stat -c %U:%G $file)" = 'root:root' ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong ownership for $file"
|
||||
logcheckresult "WARN" "Wrong ownership for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_24() {
|
||||
local id="3.24"
|
||||
local desc="Ensure that the Containerd socket file permissions are set to 660 or more restrictively (Automated)"
|
||||
local remediation="You should run the following command: chmod 660 /run/containerd/containerd.sock. This sets the file permissions for this file to 660."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
file="/run/containerd/containerd.sock"
|
||||
if [ -S "$file" ]; then
|
||||
if [ "$(stat -c %a $file)" -le 660 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
warn " * Wrong permissions for $file"
|
||||
logcheckresult "WARN" "Wrong permissions for $file"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
info " * File not found"
|
||||
logcheckresult "INFO" "File not found"
|
||||
}
|
||||
|
||||
check_3_end() {
|
||||
endsectionjson
|
||||
}
|
||||
else
|
||||
info "$check_3_20"
|
||||
info " * File not found"
|
||||
fi
|
||||
|
|
|
|||
|
|
@ -1,260 +1,133 @@
|
|||
#!/bin/bash
|
||||
#!/bin/sh
|
||||
|
||||
check_4() {
|
||||
logit ""
|
||||
local id="4"
|
||||
local desc="Container Images and Build File"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
logit "\n"
|
||||
info "4 - Container Images and Build Files"
|
||||
|
||||
check_4_1() {
|
||||
local id="4.1"
|
||||
local desc="Ensure that a user for the container has been created (Automated)"
|
||||
local remediation="You should ensure that the Dockerfile for each container image contains the information: USER <username or ID>. If there is no specific user created in the container base image, then make use of the useradd command to add a specific user before the USER instruction in the Dockerfile."
|
||||
local remediationImpact="Running as a non-root user can present challenges where you wish to bind mount volumes from the underlying host. In this case, care should be taken to ensure that the user running the contained process can read and write to the bound directory, according to their requirements."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 4.1
|
||||
check_4_1="4.1 - Create a user for the container"
|
||||
|
||||
# If container_users is empty, there are no running containers
|
||||
if [ -z "$containers" ]; then
|
||||
info -c "$check"
|
||||
info " * No containers running"
|
||||
logcheckresult "INFO" "No containers running"
|
||||
return
|
||||
fi
|
||||
# If container_users is empty, there are no running containers
|
||||
if [ -z "$containers" ]; then
|
||||
info "$check_4_1"
|
||||
info " * No containers running"
|
||||
else
|
||||
# We have some containers running, set failure flag to 0. Check for Users.
|
||||
fail=0
|
||||
# Make the loop separator be a new-line in POSIX compliant fashion
|
||||
set -f; IFS=$'
|
||||
'
|
||||
root_containers=""
|
||||
'
|
||||
for c in $containers; do
|
||||
user=$(docker inspect --format 'User={{.Config.User}}' "$c")
|
||||
|
||||
if [ "$user" = "User=0" ] || [ "$user" = "User=root" ] || [ "$user" = "User=" ] || [ "$user" = "User=[]" ] || [ "$user" = "User=<no value>" ]; then
|
||||
if [ "$user" = "User=" -o "$user" = "User=[]" -o "$user" = "User=<no value>" ]; then
|
||||
# If it's the first container, fail the test
|
||||
if [ $fail -eq 0 ]; then
|
||||
warn -s "$check"
|
||||
warn "$check_4_1"
|
||||
warn " * Running as root: $c"
|
||||
root_containers="$root_containers $c"
|
||||
fail=1
|
||||
continue
|
||||
else
|
||||
warn " * Running as root: $c"
|
||||
fi
|
||||
warn " * Running as root: $c"
|
||||
root_containers="$root_containers $c"
|
||||
fi
|
||||
done
|
||||
# We went through all the containers and found none running as root
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
pass "$check_4_1"
|
||||
fi
|
||||
logcheckresult "WARN" "running as root" "$root_containers"
|
||||
# Make the loop separator go back to space
|
||||
set +f; unset IFS
|
||||
}
|
||||
fi
|
||||
# Make the loop separator go back to space
|
||||
set +f; unset IFS
|
||||
|
||||
check_4_2() {
|
||||
local id="4.2"
|
||||
local desc="Ensure that containers use only trusted base images (Manual)"
|
||||
local remediation="Configure and use Docker Content trust. View the history of each Docker image to evaluate its risk, dependent on the sensitivity of the application you wish to deploy using it. Scan Docker images for vulnerabilities at regular intervals."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
images=$(docker images -q)
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
}
|
||||
# 4.2
|
||||
check_4_2="4.2 - Use trusted base images for containers"
|
||||
info "$check_4_2"
|
||||
|
||||
check_4_3() {
|
||||
local id="4.3"
|
||||
local desc="Ensure that unnecessary packages are not installed in the container (Manual)"
|
||||
local remediation="You should not install anything within the container that is not required. You should consider using a minimal base image if you can. Some of the options available include BusyBox and Alpine. Not only can this trim your image size considerably, but there would also be fewer pieces of software which could contain vectors for attack."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 4.3
|
||||
check_4_3="4.3 - Do not install unnecessary packages in the container"
|
||||
info "$check_4_3"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
}
|
||||
# 4.4
|
||||
check_4_4="4.4 - Scan and rebuild the images to include security patches"
|
||||
info "$check_4_4"
|
||||
|
||||
check_4_4() {
|
||||
local id="4.4"
|
||||
local desc="Ensure images are scanned and rebuilt to include security patches (Manual)"
|
||||
local remediation="Images should be re-built ensuring that the latest version of the base images are used, to keep the operating system patch level at an appropriate level. Once the images have been re-built, containers should be re-started making use of the updated images."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 4.5
|
||||
check_4_5="4.5 - Enable Content trust for Docker"
|
||||
if [ "x$DOCKER_CONTENT_TRUST" = "x1" ]; then
|
||||
pass "$check_4_5"
|
||||
else
|
||||
warn "$check_4_5"
|
||||
fi
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
}
|
||||
|
||||
check_4_5() {
|
||||
local id="4.5"
|
||||
local desc="Ensure Content trust for Docker is Enabled (Automated)"
|
||||
local remediation="Add DOCKER_CONTENT_TRUST variable to the /etc/environment file using command echo DOCKER_CONTENT_TRUST=1 | sudo tee -a /etc/environment."
|
||||
local remediationImpact="This prevents users from working with tagged images unless they contain a signature."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if [ "$DOCKER_CONTENT_TRUST" = "1" ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
|
||||
check_4_6() {
|
||||
local id="4.6"
|
||||
local desc="Ensure that HEALTHCHECK instructions have been added to container images (Automated)"
|
||||
local remediation="You should follow the Docker documentation and rebuild your container images to include the HEALTHCHECK instruction."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
no_health_images=""
|
||||
for img in $images; do
|
||||
if docker inspect --format='{{.Config.Healthcheck}}' "$img" 2>/dev/null | grep -e "<nil>" >/dev/null 2>&1; then
|
||||
if [ $fail -eq 0 ]; then
|
||||
fail=1
|
||||
warn -s "$check"
|
||||
fi
|
||||
imgName=$(docker inspect --format='{{.RepoTags}}' "$img" 2>/dev/null)
|
||||
if ! [ "$imgName" = '[]' ]; then
|
||||
warn " * No Healthcheck found: $imgName"
|
||||
no_health_images="$no_health_images $imgName"
|
||||
else
|
||||
warn " * No Healthcheck found: $img"
|
||||
no_health_images="$no_health_images $img"
|
||||
fi
|
||||
# 4.6
|
||||
check_4_6="4.6 - Add HEALTHCHECK instruction to the container image"
|
||||
fail=0
|
||||
for img in $images; do
|
||||
docker inspect --format='{{.Config.Healthcheck}}' "$img" 2>/dev/null | grep -e "<nil>" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
if [ $fail -eq 0 ]; then
|
||||
fail=1
|
||||
warn "$check_4_6"
|
||||
fi
|
||||
done
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "WARN" "Images w/o HEALTHCHECK" "$no_health_images"
|
||||
}
|
||||
|
||||
check_4_7() {
|
||||
local id="4.7"
|
||||
local desc="Ensure update instructions are not used alone in the Dockerfile (Manual)"
|
||||
local remediation="You should use update instructions together with install instructions and version pinning for packages while installing them. This prevent caching and force the extraction of the required versions. Alternatively, you could use the --no-cache flag during the docker build process to avoid using cached layers."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
update_images=""
|
||||
for img in $images; do
|
||||
if docker history "$img" 2>/dev/null | grep -e "update" >/dev/null 2>&1; then
|
||||
if [ $fail -eq 0 ]; then
|
||||
fail=1
|
||||
info -c "$check"
|
||||
fi
|
||||
imgName=$(docker inspect --format='{{.RepoTags}}' "$img" 2>/dev/null)
|
||||
if ! [ "$imgName" = '[]' ]; then
|
||||
info " * Update instruction found: $imgName"
|
||||
update_images="$update_images $imgName"
|
||||
fi
|
||||
imgName=$(docker inspect --format='{{.RepoTags}}' "$img" 2>/dev/null)
|
||||
if ! [ "$imgName" = '[]' ]; then
|
||||
warn " * No Healthcheck found: $imgName"
|
||||
fi
|
||||
done
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "INFO" "Update instructions found" "$update_images"
|
||||
}
|
||||
done
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass "$check_4_6"
|
||||
fi
|
||||
|
||||
check_4_8() {
|
||||
local id="4.8"
|
||||
local desc="Ensure setuid and setgid permissions are removed (Manual)"
|
||||
local remediation="You should allow setuid and setgid permissions only on executables which require them. You could remove these permissions at build time by adding the following command in your Dockerfile, preferably towards the end of the Dockerfile: RUN find / -perm /6000 -type f -exec chmod a-s {} ; || true"
|
||||
local remediationImpact="The above command would break all executables that depend on setuid or setgid permissions including legitimate ones. You should therefore be careful to modify the command to suit your requirements so that it does not reduce the permissions of legitimate programs excessively. Because of this, you should exercise a degree of caution and examine all processes carefully before making this type of modification in order to avoid outages."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
}
|
||||
|
||||
check_4_9() {
|
||||
local id="4.9"
|
||||
local desc="Ensure that COPY is used instead of ADD in Dockerfiles (Manual)"
|
||||
local remediation="You should use COPY rather than ADD instructions in Dockerfiles."
|
||||
local remediationImpact="Care needs to be taken in implementing this control if the application requires functionality that is part of the ADD instruction, for example, if you need to retrieve files from remote URLS."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
add_images=""
|
||||
for img in $images; do
|
||||
if docker history --format "{{ .CreatedBy }}" --no-trunc "$img" | \
|
||||
sed '$d' | grep -q 'ADD'; then
|
||||
if [ $fail -eq 0 ]; then
|
||||
fail=1
|
||||
info -c "$check"
|
||||
fi
|
||||
imgName=$(docker inspect --format='{{.RepoTags}}' "$img" 2>/dev/null)
|
||||
if ! [ "$imgName" = '[]' ]; then
|
||||
info " * ADD in image history: $imgName"
|
||||
add_images="$add_images $imgName"
|
||||
fi
|
||||
# 4.7
|
||||
check_4_7="4.7 - Do not use update instructions alone in the Dockerfile"
|
||||
fail=0
|
||||
for img in $images; do
|
||||
docker history "$img" 2>/dev/null | grep -e "update" >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
if [ $fail -eq 0 ]; then
|
||||
fail=1
|
||||
info "$check_4_7"
|
||||
fi
|
||||
imgName=$(docker inspect --format='{{.RepoTags}}' "$img" 2>/dev/null)
|
||||
if ! [ "$imgName" = '[]' ]; then
|
||||
info " * Update instruction found: $imgName"
|
||||
fi
|
||||
done
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "INFO" "Images using ADD" "$add_images"
|
||||
}
|
||||
done
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass "$check_4_7"
|
||||
fi
|
||||
|
||||
check_4_10() {
|
||||
local id="4.10"
|
||||
local desc="Ensure secrets are not stored in Dockerfiles (Manual)"
|
||||
local remediation="Do not store any kind of secrets within Dockerfiles. Where secrets are required during the build process, make use of a secrets management tool, such as the buildkit builder included with Docker."
|
||||
local remediationImpact="A proper secrets management process will be required for Docker image building."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 4.8
|
||||
check_4_8="4.8 - Remove setuid and setgid permissions in the images"
|
||||
info "$check_4_8"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
}
|
||||
# 4.9
|
||||
check_4_9="4.9 - Use COPY instead of ADD in Dockerfile"
|
||||
fail=0
|
||||
for img in $images; do
|
||||
docker history "$img" 2> /dev/null | grep 'ADD' >/dev/null 2>&1
|
||||
if [ $? -eq 0 ]; then
|
||||
if [ $fail -eq 0 ]; then
|
||||
fail=1
|
||||
info "$check_4_9"
|
||||
fi
|
||||
imgName=$(docker inspect --format='{{.RepoTags}}' "$img" 2>/dev/null)
|
||||
if ! [ "$imgName" = '[]' ]; then
|
||||
info " * ADD in image history: $imgName"
|
||||
fi
|
||||
fi
|
||||
done
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass "$check_4_9"
|
||||
fi
|
||||
|
||||
check_4_11() {
|
||||
local id="4.11"
|
||||
local desc="Ensure only verified packages are installed (Manual)"
|
||||
local remediation="You should use a secure package distribution mechanism of your choice to ensure the authenticity of software packages."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 4.10
|
||||
check_4_10="4.10 - Do not store secrets in Dockerfiles"
|
||||
info "$check_4_10"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
}
|
||||
|
||||
check_4_12() {
|
||||
local id="4.12"
|
||||
local desc="Ensure all signed artifacts are validated (Manual)"
|
||||
local remediation="Validate artifacts signatures before uploading to the package registry."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
}
|
||||
|
||||
check_4_end() {
|
||||
endsectionjson
|
||||
}
|
||||
# 4.11
|
||||
check_4_11="4.11 - Install verified packages only"
|
||||
info "$check_4_11"
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load diff
|
|
@ -1,60 +1,47 @@
|
|||
#!/bin/bash
|
||||
#!/bin/sh
|
||||
|
||||
check_6() {
|
||||
logit ""
|
||||
local id="6"
|
||||
local desc="Docker Security Operations"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
logit "\n"
|
||||
info "6 - Docker Security Operations"
|
||||
|
||||
check_6_1() {
|
||||
local id="6.1"
|
||||
local desc="Ensure that image sprawl is avoided (Manual)"
|
||||
local remediation="You should keep only the images that you actually need and establish a workflow to remove old or stale images from the host. Additionally, you should use features such as pull-by-digest to get specific images from the registry."
|
||||
local remediationImpact="docker system prune -a removes all exited containers as well as all images and volumes that are not referenced by running containers, including for UCP and DTR."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
# 6.1
|
||||
check_6_1="6.1 - Perform regular security audits of your host system and containers"
|
||||
info "$check_6_1"
|
||||
|
||||
images=$(docker images -q | sort -u | wc -l | awk '{print $1}')
|
||||
active_images=0
|
||||
# 6.2
|
||||
check_6_2="6.2 - Monitor Docker containers usage, performance and metering"
|
||||
info "$check_6_2"
|
||||
|
||||
for c in $(docker inspect --format "{{.Image}}" $(docker ps -qa) 2>/dev/null); do
|
||||
if docker images --no-trunc -a | grep "$c" > /dev/null ; then
|
||||
active_images=$(( active_images += 1 ))
|
||||
fi
|
||||
done
|
||||
# 6.3
|
||||
check_6_3="6.3 - Backup container data"
|
||||
info "$check_6_3"
|
||||
|
||||
info -c "$check"
|
||||
# 6.4
|
||||
check_6_4="6.4 - Avoid image sprawl"
|
||||
images=$(docker images -q | sort -u | wc -l | awk '{print $1}')
|
||||
active_images=0
|
||||
|
||||
for c in $(docker inspect -f "{{.Image}}" $(docker ps -qa)); do
|
||||
if docker images --no-trunc -a | grep "$c" > /dev/null ; then
|
||||
active_images=$(( active_images += 1 ))
|
||||
fi
|
||||
done
|
||||
|
||||
info "$check_6_4"
|
||||
info " * There are currently: $images images"
|
||||
|
||||
if [ "$active_images" -lt "$((images / 2))" ]; then
|
||||
info " * Only $active_images out of $images are in use"
|
||||
fi
|
||||
logcheckresult "INFO" "$active_images active/$images in use"
|
||||
}
|
||||
if [ "$active_images" -lt "$((images / 2))" ]; then
|
||||
info " * Only $active_images out of $images are in use"
|
||||
fi
|
||||
|
||||
check_6_2() {
|
||||
local id="6.2"
|
||||
local desc="Ensure that container sprawl is avoided (Manual)"
|
||||
local remediation="You should periodically check your container inventory on each host and clean up containers which are not in active use with the command: docker container prune"
|
||||
local remediationImpact="You should retain containers that are actively in use, and delete ones which are no longer needed."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
total_containers=$(docker info 2>/dev/null | grep "Containers" | awk '{print $2}')
|
||||
running_containers=$(docker ps -q | wc -l | awk '{print $1}')
|
||||
diff="$((total_containers - running_containers))"
|
||||
info -c "$check"
|
||||
if [ "$diff" -gt 25 ]; then
|
||||
info " * There are currently a total of $total_containers containers, with only $running_containers of them currently running"
|
||||
else
|
||||
info " * There are currently a total of $total_containers containers, with $running_containers of them currently running"
|
||||
fi
|
||||
logcheckresult "INFO" "$total_containers total/$running_containers running"
|
||||
}
|
||||
|
||||
check_6_end() {
|
||||
endsectionjson
|
||||
}
|
||||
# 6.5
|
||||
check_6_5="6.5 - Avoid container sprawl"
|
||||
total_containers=$(docker info 2>/dev/null | grep "Containers" | awk '{print $2}')
|
||||
running_containers=$(docker ps -q | wc -l | awk '{print $1}')
|
||||
diff="$((total_containers - running_containers))"
|
||||
if [ "$diff" -gt 25 ]; then
|
||||
info "$check_6_5"
|
||||
info " * There are currently a total of $total_containers containers, with only $running_containers of them currently running"
|
||||
else
|
||||
info "$check_6_5"
|
||||
info " * There are currently a total of $total_containers containers, with $running_containers of them currently running"
|
||||
fi
|
||||
|
|
|
|||
|
|
@ -1,208 +0,0 @@
|
|||
#!/bin/bash
|
||||
|
||||
check_7() {
|
||||
logit ""
|
||||
local id="7"
|
||||
local desc="Docker Swarm Configuration"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
|
||||
check_7_1() {
|
||||
local id="7.1"
|
||||
local desc="Ensure that the minimum number of manager nodes have been created in a swarm (Automated)"
|
||||
local remediation="If an excessive number of managers is configured, the excess nodes can be demoted to workers using command: docker node demote <manager node ID to be demoted>"
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:*\sactive\s*" >/dev/null 2>&1; then
|
||||
managernodes=$(docker node ls | grep -c "Leader")
|
||||
if [ "$managernodes" -eq 1 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_2() {
|
||||
local id="7.2"
|
||||
local desc="Ensure that swarm services are bound to a specific host interface (Automated)"
|
||||
local remediation="Resolving this issues requires re-initialization of the swarm, specifying a specific interface for the --listen-addr parameter."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:*\sactive\s*" >/dev/null 2>&1; then
|
||||
$netbin -lnt | grep -e '\[::]:2377 ' -e ':::2377' -e '*:2377 ' -e ' 0\.0\.0\.0:2377 ' >/dev/null 2>&1
|
||||
if [ $? -eq 1 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_3() {
|
||||
local id="7.3"
|
||||
local desc="Ensure that all Docker swarm overlay networks are encrypted (Automated)"
|
||||
local remediation="You should create overlay networks the with --opt encrypted flag."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
unencrypted_networks=""
|
||||
for encnet in $(docker network ls --filter driver=overlay --quiet); do
|
||||
if docker network inspect --format '{{.Name}} {{ .Options }}' "$encnet" | \
|
||||
grep -v 'encrypted:' 2>/dev/null 1>&2; then
|
||||
# If it's the first container, fail the test
|
||||
if [ $fail -eq 0 ]; then
|
||||
warn -s "$check"
|
||||
fail=1
|
||||
fi
|
||||
warn " * Unencrypted overlay network: $(docker network inspect --format '{{ .Name }} ({{ .Scope }})' "$encnet")"
|
||||
unencrypted_networks="$unencrypted_networks $(docker network inspect --format '{{ .Name }} ({{ .Scope }})' "$encnet")"
|
||||
fi
|
||||
done
|
||||
# We went through all the networks and found none that are unencrypted
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "WARN" "Unencrypted overlay networks:" "$unencrypted_networks"
|
||||
}
|
||||
|
||||
check_7_4() {
|
||||
local id="7.4"
|
||||
local desc="Ensure that Docker's secret management commands are used for managing secrets in a swarm cluster (Manual)"
|
||||
local remediation="You should follow the docker secret documentation and use it to manage secrets effectively."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
if [ "$(docker secret ls -q | wc -l)" -ge 1 ]; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
return
|
||||
fi
|
||||
pass -c "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_5() {
|
||||
local id="7.5"
|
||||
local desc="Ensure that swarm manager is run in auto-lock mode (Automated)"
|
||||
local remediation="If you are initializing a swarm, use the command: docker swarm init --autolock. If you want to set --autolock on an existing swarm manager node, use the command: docker swarm update --autolock."
|
||||
local remediationImpact="A swarm in auto-lock mode will not recover from a restart without manual intervention from an administrator to enter the unlock key. This may not always be desirable, and should be reviewed at a policy level."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
if ! docker swarm unlock-key 2>/dev/null | grep 'SWMKEY' 2>/dev/null 1>&2; then
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
pass -s "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_6() {
|
||||
local id="7.6"
|
||||
local desc="Ensure that the swarm manager auto-lock key is rotated periodically (Manual)"
|
||||
local remediation="You should run the command docker swarm unlock-key --rotate to rotate the keys. To facilitate auditing of this recommendation, you should maintain key rotation records and ensure that you establish a pre-defined frequency for key rotation."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
note -c "$check"
|
||||
logcheckresult "NOTE"
|
||||
return
|
||||
fi
|
||||
pass -c "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_7() {
|
||||
local id="7.7"
|
||||
local desc="Ensure that node certificates are rotated as appropriate (Manual)"
|
||||
local remediation="You should run the command docker swarm update --cert-expiry 48h to set the desired expiry time on the node certificate."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
if docker info 2>/dev/null | grep "Expiry Duration: 2 days"; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
return
|
||||
fi
|
||||
pass -c "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_8() {
|
||||
local id="7.8"
|
||||
local desc="Ensure that CA certificates are rotated as appropriate (Manual)"
|
||||
local remediation="You should run the command docker swarm ca --rotate to rotate a certificate."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
return
|
||||
fi
|
||||
pass -c "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_9() {
|
||||
local id="7.9"
|
||||
local desc="Ensure that management plane traffic is separated from data plane traffic (Manual)"
|
||||
local remediation="You should initialize the swarm with dedicated interfaces for management and data planes respectively. Example: docker swarm init --advertise-addr=192.168.0.1 --data-path-addr=17.1.0.3"
|
||||
local remediationImpact="This requires two network interfaces per node."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info 2>/dev/null | grep -e "Swarm:\s*active\s*" >/dev/null 2>&1; then
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
return
|
||||
fi
|
||||
pass -c "$check (Swarm mode not enabled)"
|
||||
logcheckresult "PASS"
|
||||
}
|
||||
|
||||
check_7_end() {
|
||||
endsectionjson
|
||||
}
|
||||
|
|
@ -1,170 +0,0 @@
|
|||
#!/bin/bash
|
||||
|
||||
check_8() {
|
||||
logit ""
|
||||
local id="8"
|
||||
local desc="Docker Enterprise Configuration"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
|
||||
check_product_license() {
|
||||
enterprise_license=1
|
||||
if docker version | grep -Eqi '^Server.*Community$|Version.*-ce$'; then
|
||||
info " * Community Engine license, skipping section 8"
|
||||
enterprise_license=0
|
||||
fi
|
||||
}
|
||||
|
||||
check_8_1() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1"
|
||||
local desc="Universal Control Plane Configuration"
|
||||
local check="$id - $desc"
|
||||
info "$check"
|
||||
}
|
||||
|
||||
check_8_1_1() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1.1"
|
||||
local desc="Configure the LDAP authentication service (Automated)"
|
||||
local remediation="You can configure LDAP integration via the UCP Admin Settings UI. LDAP integration can also be enabled via a configuration file"
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_1_2() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1.2"
|
||||
local desc="Use external certificates (Automated)"
|
||||
local remediation="You can configure your own certificates for UCP either during installation or after installation via the UCP Admin Settings user interface."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_1_3() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1.3"
|
||||
local desc="Enforce the use of client certificate bundles for unprivileged users (Not Scored)"
|
||||
local remediation="Client certificate bundles can be created in one of two ways. User Management UI: UCP Administrators can provision client certificate bundles on behalf of users. Self-Provision: Users with access to the UCP console can create client certificate bundles themselves."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_1_4() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1.4"
|
||||
local desc="Configure applicable cluster role-based access control policies (Not Scored)"
|
||||
local remediation="UCP RBAC components can be configured as required via the UCP User Management UI."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_1_5() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1.5"
|
||||
local desc="Enable signed image enforcement (Automated)"
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_1_6() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1.6"
|
||||
local desc="Set the Per-User Session Limit to a value of '3' or lower (Automated)"
|
||||
local remediation="Retrieve a UCP API token. Retrieve and save UCP config. Open the ucp-config.toml file, set the per_user_limit entry under the [auth.sessions] section to a value of 3 or lower, but greater than 0. Update UCP with the new configuration."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_1_7() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.1.7"
|
||||
local desc="Set the 'Lifetime Minutes' and 'Renewal Threshold Minutes' values to '15' or lower and '0' respectively (Automated)"
|
||||
local remediation="Retrieve a UCP API token. Retrieve and save UCP config. Open the ucp-config.toml file, set the lifetime_minutes and renewal_threshold_minutes entries under the [auth.sessions] section to values of 15 or lower and 0 respectively. Update UCP with the new configuration."
|
||||
local remediationImpact="Setting the Lifetime Minutes setting to a value that is too lower would result in users having to constantly re-authenticate to their Docker Enterprise cluster."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_2() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.2"
|
||||
local desc="Docker Trusted Registry Configuration"
|
||||
local check="$id - $desc"
|
||||
info "$check"
|
||||
}
|
||||
|
||||
check_8_2_1() {
|
||||
if [ "$enterprise_license" -ne 1 ]; then
|
||||
return
|
||||
fi
|
||||
|
||||
local id="8.2.1"
|
||||
local desc="Enable image vulnerability scanning (Automated)"
|
||||
local remediation="You can navigate to DTR Settings UI and select the Security tab to access the image scanning configuration. Select the Enable Scanning slider to enable this functionality."
|
||||
local remediationImpact="None."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
note -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_8_end() {
|
||||
endsectionjson
|
||||
}
|
||||
|
|
@ -1,234 +0,0 @@
|
|||
#!/bin/bash
|
||||
|
||||
check_c() {
|
||||
logit ""
|
||||
local id="99"
|
||||
local desc="Community contributed checks"
|
||||
checkHeader="$id - $desc"
|
||||
info "$checkHeader"
|
||||
startsectionjson "$id" "$desc"
|
||||
}
|
||||
|
||||
check_c_1() {
|
||||
local id="C.1"
|
||||
local desc="This is a example check for a Automated check"
|
||||
local remediation="This is an example remediation measure for a Automated check"
|
||||
local remediationImpact="This is an example remediation impact for a Automated check"
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info --format='{{ .Architecture }}' | grep 'x86_64' 2>/dev/null 1>&2; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if docker info --format='{{ .Architecture }}' | grep 'aarch64' 2>/dev/null 1>&2; then
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
|
||||
check_c_1_1() {
|
||||
local id="C.1.1"
|
||||
local desc="This is a example check for a Manual check"
|
||||
local remediation="This is an example remediation measure for a Manual check"
|
||||
local remediationImpact="This is an example remediation impact for a Manual check"
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if docker info --format='{{ .Architecture }}' | grep 'x86_64' 2>/dev/null 1>&2; then
|
||||
pass -c "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if docker info --format='{{ .Architecture }}' | grep 'aarch64' 2>/dev/null 1>&2; then
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
return
|
||||
fi
|
||||
warn -c "$check"
|
||||
logcheckresult "WARN"
|
||||
}
|
||||
|
||||
check_c_2() {
|
||||
docker_version=$(docker version | grep -i -A2 '^server' | grep ' Version:' \
|
||||
| awk '{print $NF; exit}' | tr -d '[:alpha:]-,.' | cut -c 1-4)
|
||||
|
||||
local id="C.2"
|
||||
local desc="Ensure operations on legacy registry (v1) are Disabled"
|
||||
local remediation="Start docker daemon with --disable-legacy-registry=false flag. Starting with Docker 17.12, support for V1 registries has been removed, and the --disable-legacy-registry flag can no longer be used."
|
||||
local remediationImpact="Prevents the docker daemon from pull, push, and login operations against v1 registries."
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
if [ "$docker_version" -lt 1712 ]; then
|
||||
if get_docker_configuration_file_args 'disable-legacy-registry' | grep 'true' >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
if get_docker_effective_command_line_args '--disable-legacy-registry' | grep "disable-legacy-registry" >/dev/null 2>&1; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
warn -s "$check"
|
||||
logcheckresult "WARN"
|
||||
return
|
||||
fi
|
||||
local desc="$desc (Deprecated)"
|
||||
local check="$id - $desc"
|
||||
info -c "$check"
|
||||
logcheckresult "INFO"
|
||||
}
|
||||
|
||||
check_c_5_3_1() {
|
||||
local id="C.5.3.1"
|
||||
local desc="Ensure that CAP_DAC_READ_SEARCH Linux kernel capability is disabled (Automated)"
|
||||
local remediation="Please refer to https://github.com/cdk-team/CDK/wiki/Exploit:-cap-dac-read-search for PoC."
|
||||
local remediationImpact=""
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
caps_containers=""
|
||||
for c in $containers; do
|
||||
container_caps=$(docker inspect --format 'CapAdd={{ .HostConfig.CapAdd }}' "$c")
|
||||
caps=$(echo "$container_caps" | tr "[:lower:]" "[:upper:]" | \
|
||||
sed 's/CAPADD/CapAdd/')
|
||||
if echo "$caps" | grep -q "DAC_READ_SEARCH"; then
|
||||
# If it's the first container, fail the test
|
||||
if [ $fail -eq 0 ]; then
|
||||
warn -s "$check"
|
||||
warn " * CAP_DAC_READ_SEARCH added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fail=1
|
||||
continue
|
||||
fi
|
||||
warn " * CAP_DAC_READ_SEARCH added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fi
|
||||
done
|
||||
# We went through all the containers and found none with extra capabilities
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "WARN" "CAP_DAC_READ_SEARCH capability added for containers" "$caps_containers"
|
||||
}
|
||||
|
||||
check_c_5_3_2() {
|
||||
local id="C.5.3.2"
|
||||
local desc="Ensure that CAP_SYS_MODULE Linux kernel capability is disabled (Automated)"
|
||||
local remediation="Please refer to https://xcellerator.github.io/posts/docker_escape/ for PoC."
|
||||
local remediationImpact=""
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
caps_containers=""
|
||||
for c in $containers; do
|
||||
container_caps=$(docker inspect --format 'CapAdd={{ .HostConfig.CapAdd }}' "$c")
|
||||
caps=$(echo "$container_caps" | tr "[:lower:]" "[:upper:]" | \
|
||||
sed 's/CAPADD/CapAdd/')
|
||||
if echo "$caps" | grep -q "SYS_MODULE"; then
|
||||
# If it's the first container, fail the test
|
||||
if [ $fail -eq 0 ]; then
|
||||
warn -s "$check"
|
||||
warn " * CAP_SYS_MODULE added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fail=1
|
||||
continue
|
||||
fi
|
||||
warn " * CAP_SYS_MODULE added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fi
|
||||
done
|
||||
# We went through all the containers and found none with extra capabilities
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "WARN" "CAP_SYS_MODULE capability added for containers" "$caps_containers"
|
||||
}
|
||||
|
||||
check_c_5_3_3() {
|
||||
local id="C.5.3.3"
|
||||
local desc="Ensure that CAP_SYS_ADMIN Linux kernel capability is disabled (Automated)"
|
||||
local remediation="Please refer to https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/ for PoC."
|
||||
local remediationImpact=""
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
caps_containers=""
|
||||
for c in $containers; do
|
||||
container_caps=$(docker inspect --format 'CapAdd={{ .HostConfig.CapAdd }}' "$c")
|
||||
caps=$(echo "$container_caps" | tr "[:lower:]" "[:upper:]" | \
|
||||
sed 's/CAPADD/CapAdd/')
|
||||
if echo "$caps" | grep -q "SYS_ADMIN"; then
|
||||
# If it's the first container, fail the test
|
||||
if [ $fail -eq 0 ]; then
|
||||
warn -s "$check"
|
||||
warn " * CAP_SYS_ADMIN added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fail=1
|
||||
continue
|
||||
fi
|
||||
warn " * CAP_SYS_ADMIN added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fi
|
||||
done
|
||||
# We went through all the containers and found none with extra capabilities
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "WARN" "CAP_SYS_ADMIN capability added for containers" "$caps_containers"
|
||||
}
|
||||
|
||||
check_c_5_3_4() {
|
||||
local id="C.5.3.4"
|
||||
local desc="Ensure that CAP_SYS_PTRACE Linux kernel capability is disabled (Automated)"
|
||||
local remediation="Please refer to https://0xn3va.gitbook.io/cheat-sheets/container/escaping/excessive-capabilities#cap_sys_ptrace"
|
||||
local remediationImpact=""
|
||||
local check="$id - $desc"
|
||||
starttestjson "$id" "$desc"
|
||||
|
||||
fail=0
|
||||
caps_containers=""
|
||||
for c in $containers; do
|
||||
container_caps=$(docker inspect --format 'CapAdd={{ .HostConfig.CapAdd }}' "$c")
|
||||
caps=$(echo "$container_caps" | tr "[:lower:]" "[:upper:]" | \
|
||||
sed 's/CAPADD/CapAdd/')
|
||||
if echo "$caps" | grep -q "SYS_PTRACE"; then
|
||||
# If it's the first container, fail the test
|
||||
if [ $fail -eq 0 ]; then
|
||||
warn -s "$check"
|
||||
warn " * CAP_SYS_PTRACE added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fail=1
|
||||
continue
|
||||
fi
|
||||
warn " * CAP_SYS_PTRACE added to $c"
|
||||
caps_containers="$caps_containers $c"
|
||||
fi
|
||||
done
|
||||
# We went through all the containers and found none with extra capabilities
|
||||
if [ $fail -eq 0 ]; then
|
||||
pass -s "$check"
|
||||
logcheckresult "PASS"
|
||||
return
|
||||
fi
|
||||
logcheckresult "WARN" "CAP_SYS_PTRACE capability added for containers" "$caps_containers"
|
||||
}
|
||||
|
||||
check_c_end() {
|
||||
endsectionjson
|
||||
}
|
||||
Loading…
Add table
Add a link
Reference in a new issue